
Most Commonly Used Linux Commands You Should Know
Linux is a very popular Operating System (OS) amongst programmers and regular users. One of the main reasons for its popularity is its exceptional command line support. We can manage the entire Linux operating system via command line interface (CLI)
Jun 28, 2025 am 10:53 AM
How to Install Lua Scripting Language in Linux
Lua is a free and open-source, robust, minimal, embeddable, and powerful scripting language. It is an interpreted, dynamically typed, extensible scripting language that runs by interpreting bytecode using a register-based virtual machine.Lua works on
Jun 28, 2025 am 10:48 AM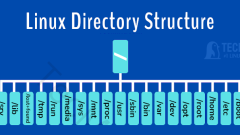
Understanding Linux Directory Structure and Important Files
Brief: This article gives a breakdown of the Linux File System/directory structure, some of the critical files, their usability, and their location. You must have probably heard that everything is considered a file in UNIX and UNIX derivatives such a
Jun 28, 2025 am 10:26 AM
Monitor Linux Users Activity with psacct or acct Tools
psacct or acct both are open source utilities for monitoring users’ activities on the Linux system. These utilities run in the background and keep track of each user’s activity on your system as well as what resources are being consumed. I pe
Jun 28, 2025 am 10:17 AM
5 Best Practices to Prevent SSH Brute-Force Login Attacks
Servers running SSH are often considered easy targets for brute-force attacks. Cybercriminals continue to develop new software and bots that automate these types of attacks, increasing the likelihood of unauthorized access.In this article, we’ll look
Jun 28, 2025 am 10:13 AM
Most Common SSH Command Usage and Configuration in Linux
Brief: In this guide, we will discuss the common use cases of SSH. We will also discuss commonly used SSH configurations that can be used in day-to-day life to boost your productivity. Secure Shell (SSH) is a widely adopted network protocol, which al
Jun 28, 2025 am 09:59 AM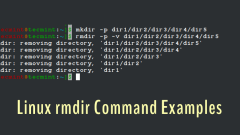
Linux rmdir Command Examples for Beginners
As Linux users, we interact with the files and directories on a regular basis. One common operation users perform is removing directories from the file system. However, we have to be extra careful while removing the directories. Because carelessly pe
Jun 28, 2025 am 09:38 AM
Most Common Network Port Numbers for Linux
In computing, particularly in TCP/IP and UDP networks, a port is a logical address typically assigned to a specific service or running application on a computer. It acts as a connection endpoint that directs traffic to a particular service within the
Jun 28, 2025 am 09:35 AM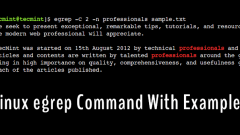
20 Useful egrep Command Examples in Linux
Brief: In this guide, we will discuss some of the practical examples of the egrep command. After following this guide, users will be able to perform text searching more efficiently in Linux. Have you ever been frustrated because you are unable to fin
Jun 28, 2025 am 09:23 AM
How to move or rename a file in Linux
In Linux, use the mv command to move or rename files. 1. When moving the file, the syntax is the target path of the mv source file path. If the target path is an existing directory, the file will be moved in, otherwise renaming will be attempted; 2. Renaming is achieved by specifying a new name in the same directory, such as mvoldname.txtnewname.txt; 3. Use the -i parameter to confirm before overwriting, and -n can prevent overwriting; 4. Support batch operations, such as mvfile1.txtfile2.txt/target/dir/; 5. Adding the -v parameter to display operation details; 6. Sudo can be used to upgrade the authority when there is insufficient permissions.
Jun 28, 2025 am 12:49 AM
What is the purpose of getopts?
getopts is a tool for parsing command line options in shell scripts, which provides a structured and reliable way to handle short options like -f. ① It loops through the command line parameters received by the script and assigns each parameter to the variable according to the definition; ② Supports option grouping (such as -abc) and parameterized options (such as -avalue); ③ Automatically handle invalid options and set OPTARG and OPTIND variables to save the current option parameters and index positions respectively; ④ When using it, please note that only short options are supported, options must be prefixed, and the remaining parameters must be processed using the shift command correctly. For example, use shift$((OPTIND-1)) to obtain non-optional parameters.
Jun 28, 2025 am 12:48 AM
How to find my IP address in Linux
There are three ways to view IP addresses in Linux: 1. Use the ipaddrshow command to view all interface information, or specify interfaces such as ipaddrshoweth0; 2. Quickly obtain all non-local loopback IPv4 addresses through hostname-I; 3. If the net-tools package is installed, you can use the ifconfig command to query. These methods are applicable to different distributions and usage scenarios.
Jun 28, 2025 am 12:41 AM
How to list the current firewall rules?
To view the current firewall rules, you need to select the corresponding commands based on the operating system and firewall tools. 1. Execute sudoiptables-L-v-n when using iptables, 2. Run sudonftlistruleset when using nftables, 3. Use sudoufw statusverbose for Ubuntu, 4. Execute sudopfctl-sr to view PF firewall rules through macOS, 5. On Windows, you can run Get-NetFirewallRule or netsh command netshadvfirewallfire through PowerShell
Jun 28, 2025 am 12:40 AM
How does a Kubernetes Ingress work?
The Ingress controller is a component responsible for implementing Ingress rules. Its working principle is to listen for Ingress resource changes and configure reverse proxy. 1. Ingress itself is only a rule definition, and the controller is the actual executor; 2. Common controllers include NGINX, Traefik, AWSALB and IstioGateway; 3. When writing Ingress, the key fields include path, pathType and backend; 4. Configuring TLS requires preparing certificates, creating Secrets and references in Ingress; 5. Frequently asked questions should check the Ingress status, controller logs and service operation status in turn.
Jun 28, 2025 am 12:38 AM
Hot tools Tags

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

vc9-vc14 (32+64 bit) runtime library collection (link below)
Download the collection of runtime libraries required for phpStudy installation

VC9 32-bit
VC9 32-bit phpstudy integrated installation environment runtime library

PHP programmer toolbox full version
Programmer Toolbox v1.0 PHP Integrated Environment

VC11 32-bit
VC11 32-bit phpstudy integrated installation environment runtime library

SublimeText3 Chinese version
Chinese version, very easy to use







