 Software Tutorial
Software Tutorial
 Mobile Application
Mobile Application
 How to intercept too many harassing calls on Apple's mobile phone 'A must-read for newbies: How to solve frequent spam text messages and harassing calls on iPhone'
How to intercept too many harassing calls on Apple's mobile phone 'A must-read for newbies: How to solve frequent spam text messages and harassing calls on iPhone'
How to intercept too many harassing calls on Apple's mobile phone 'A must-read for newbies: How to solve frequent spam text messages and harassing calls on iPhone'
Feb 06, 2024 pm 05:04 PMHow to intercept too many harassing calls on my Apple phone? PHP editor Xiaoxin brings you a detailed article to teach you how to solve the problem of frequent spam text messages and harassing phone calls on iPhone. In modern society, mobile phone harassment has become a problem for many people. It not only wastes time, but also causes unnecessary trouble. This article will introduce you to several methods of intercepting harassing calls to help you solve this problem and make your mobile phone calls quieter and more convenient. If you are new to Apple mobile phones, then this article is a must-read and I hope it will be helpful to you.
618 is approaching, and many businesses have begun to operate through text messages. You may receive several marketing text messages or other harassing calls throughout the day.

These spam text messages and phone calls will not only cause users financial losses, but also have a negative impact on study and work. What's worse is that many of them are wire scams, and even those who regularly pay attention to such issues and have the discernment skills can fall for them.
To avoid being harassed by spam text messages and phone calls or even telecom fraud, it is essential to master some settings and techniques. In actual experience, the combination of multiple settings can indeed effectively reduce the spam text messages and harassing calls received.
Interception through iPhone settings
iMessage is a major feature of iPhone, but it also brings a lot of spam text messages, which are often registered through Apple ID Sent by email.
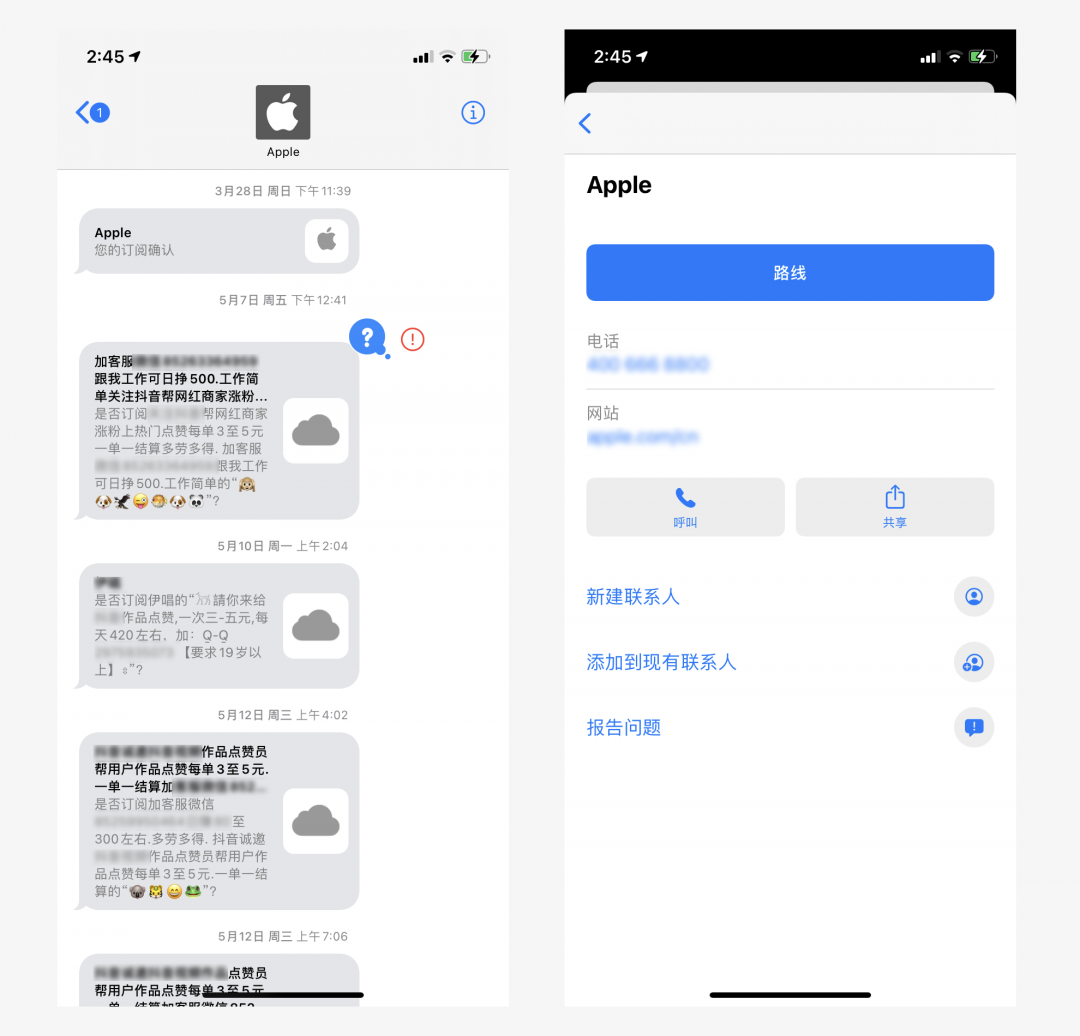

Unchecking the box to accept iMessage messages via email can reduce the number of spam iMessage messages received to a certain extent. If you don’t usually You can even turn it off directly after using it without affecting the normal text messaging function.
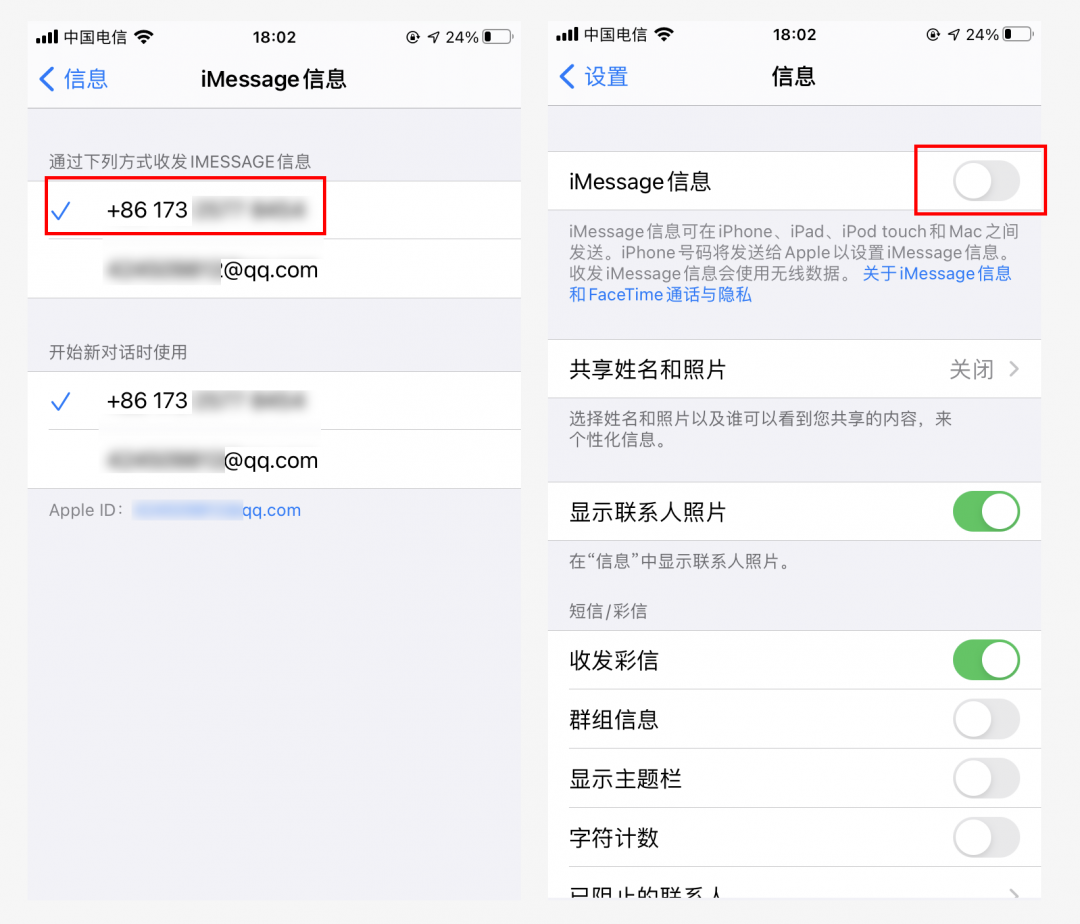

In addition, in settings, text messages, turn on filtering location senders, you can simply classify text messages that are not in the address book , and only silent reminders will be issued when receiving such text messages; you can also manually add a blacklist to blocked contacts. This setting is effective for both text messages and phone calls.
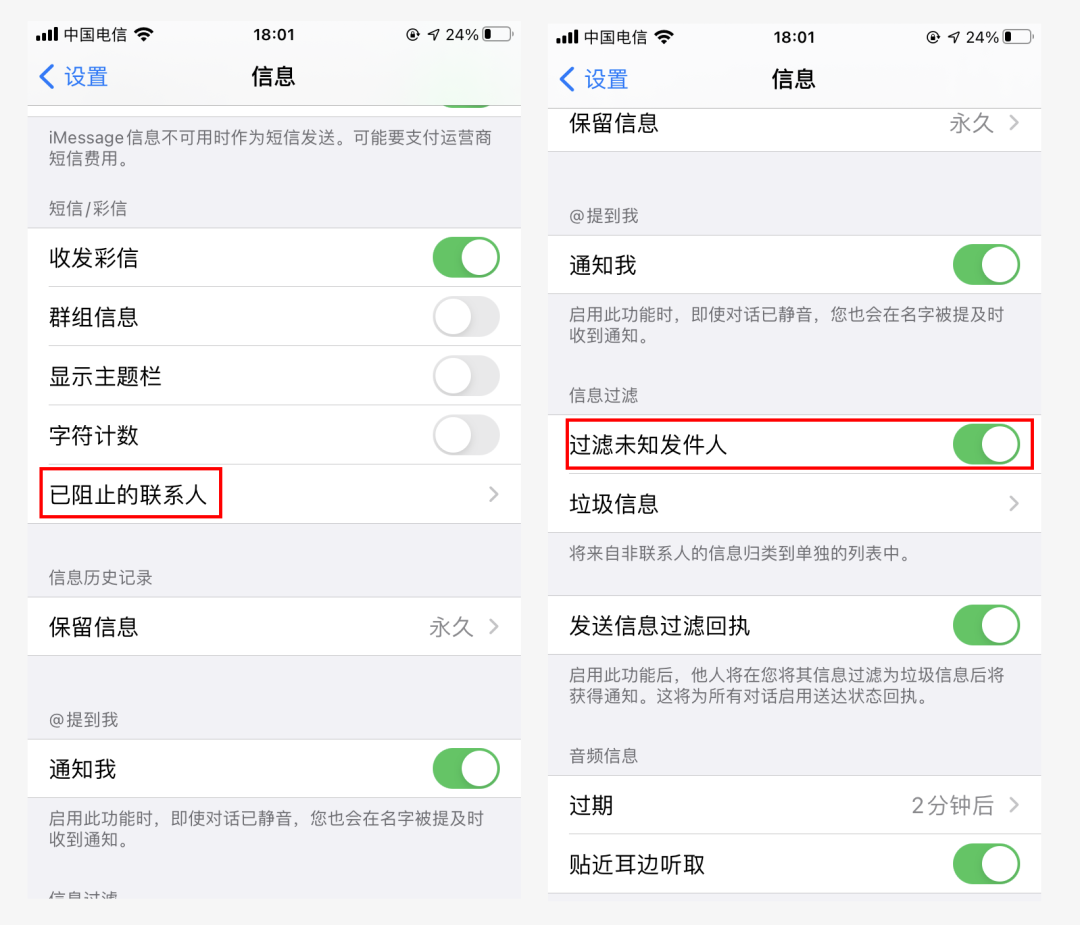

Without the installation of third-party software, iPhone can only perform simple interception, whether it is text messages or phone calls. Although Intercepting isn't smart enough, but it's better than nothing.
In fact, in terms of intercepting spam text messages and phone calls, Android phones such as Huawei and Xiaomi do a relatively good job. The text messages and calls on the mobile phones have built-in harassment interception functions, which can be customized. The interception rules and interception effects are good, and you can even automatically answer some marketing calls through the AI ??voice assistant.
Set interception through third-party APP
If you want the iPhone to have a better interception effect like other Android phones, you must use some third-party APP, such as Panda Eat SMS, Tencent Mobile Butler, etc.
Through this type of software, you can add some intelligent interception rules. For harassing calls, the database will be continuously updated, and automatic interception and custom interception can be set; for spam text messages, automatic filtering can be set and filtering keywords can be added manually (it is recommended to add "T", "TD", etc.), and you can also add Whitelist and blacklist.
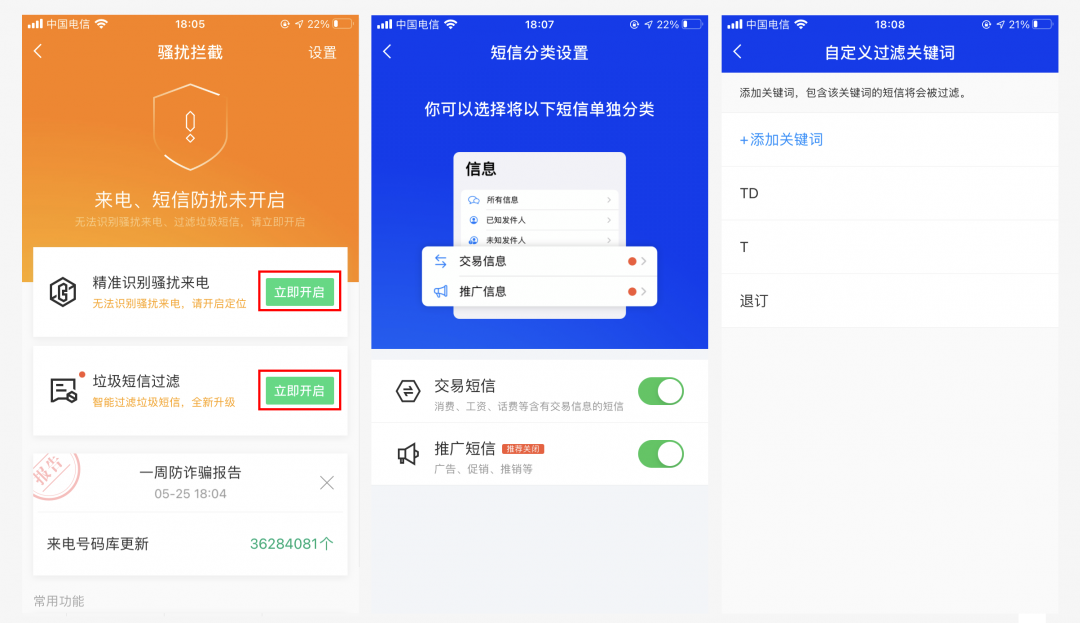

After adding the interception rules, the SMS APP will additionally display text messages intercepted and filtered by third-party software. When receiving new or past call records, it can mark part of the mobile phone number more accurately.
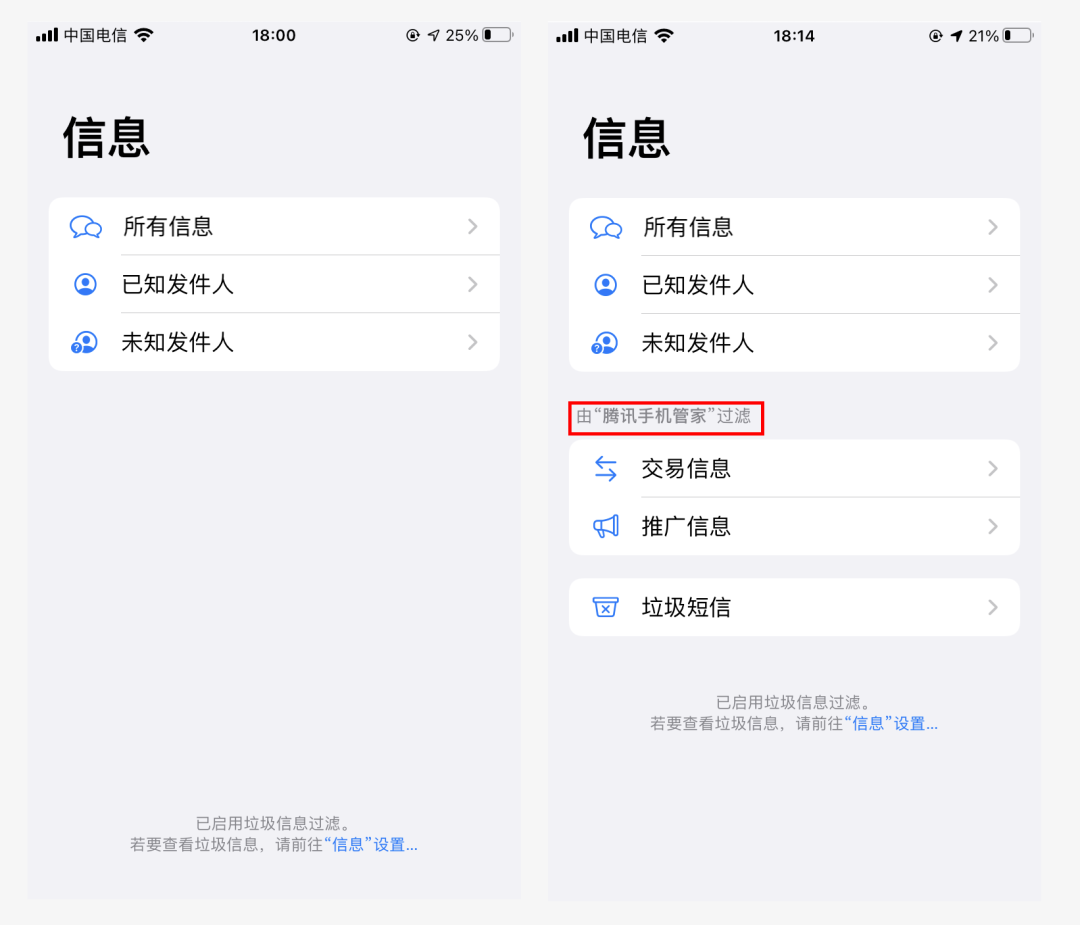

If you want to get a better interception effect, it may not be enough to intercept through a third-party APP. You can also continue to provide it through the operator interception and filtering services to improve the effectiveness of interception.
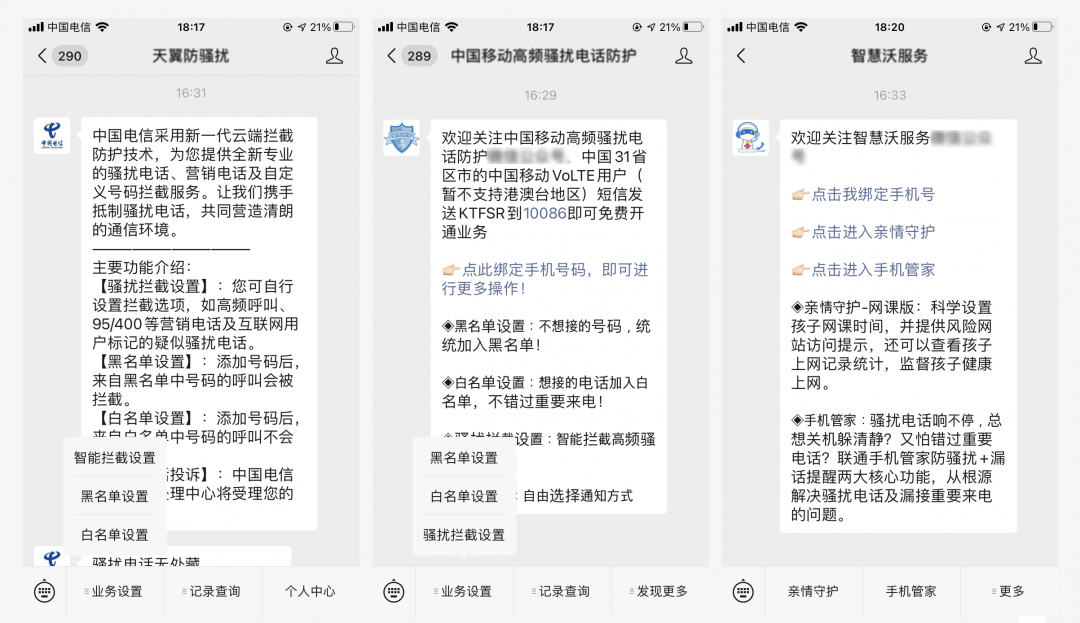
Interception through the services provided by the operator
Through the services provided by the operator, spam text messages and harassing calls can be intercepted directly from the source.
Mobile users: send "KTFSR" to 10086;
Telecom users: send SMS "KTFSR" to 10001;
Unicom users: send "KT" to 10655587, and then Send "Y" to confirm (some users may not be able to handle it).
Alternatively, you can activate and set up this function through the official accounts designated by the three major operators.

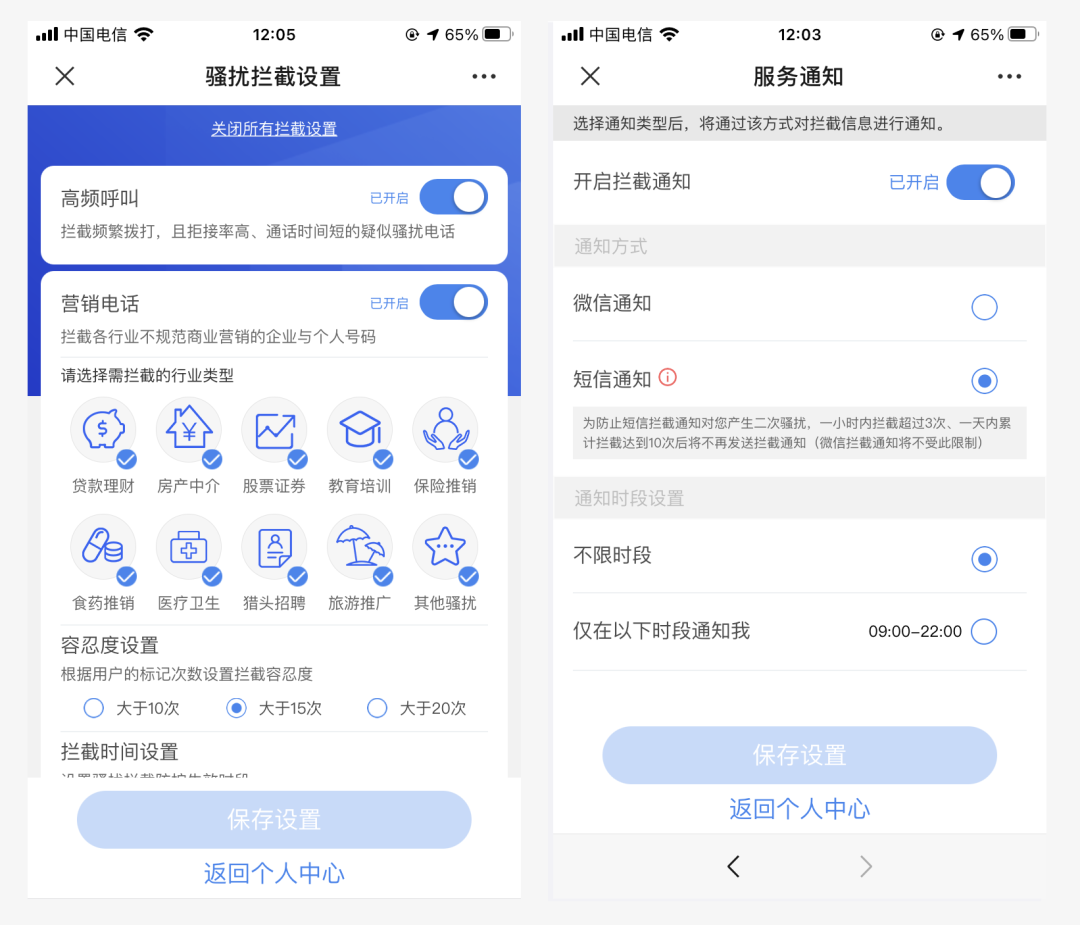
Taking telecommunications as an example, users can set the interception period, intercepted phone industry type, and even specified number segments. In the service notification, you can also choose to notify the interception status through SMS or WeChat.

Report harassment calls through the Ministry of Industry and Information Technology
If you continue to receive marketing from operators or other platforms for a period of time To use the advertising phone number (such as 10016), you can make a complaint at the Ministry of Industry and Information Technology's Network Bad Network and Spam Reporting and Acceptance Center or dial 12321.

Summary
The main reason why we receive spam text messages and harassing phone calls is because of information leakage. Daily use APP or website registration, shopping, travel, etc., and some survey activities may directly lead to the leakage of personal information.

Although in the era of big data, personal privacy protection is more difficult to guarantee, we still need to be aware of privacy protection, and when possible Be extra cautious wherever privacy leaks occur.


Intercepting spam text messages and phone calls is only the basis. Paying attention to and protecting personal privacy and information security is the ultimate goal.
The above is the detailed content of How to intercept too many harassing calls on Apple's mobile phone 'A must-read for newbies: How to solve frequent spam text messages and harassing calls on iPhone'. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to create a contact group on iPhone
Jul 13, 2025 am 01:17 AM
How to create a contact group on iPhone
Jul 13, 2025 am 01:17 AM
iPhone does not support creating contact groups directly in the address book application, but similar functions can be achieved through the following methods: 1. Use the "Group" function in the address book application, click "Edit" > "Add Group" to create a custom group; 2. Add each contact to the corresponding group by editing it; 3. If you need to send a group message, you can create a new multi-person conversation in the information application; 4. Use iCloud or Gmail to synchronize tagged groups to facilitate the management of a large number of contacts on the computer. These methods are used in conjunction with efficient management of contact groups.
 How to check if an iPhone is unlocked
Jul 15, 2025 am 01:17 AM
How to check if an iPhone is unlocked
Jul 15, 2025 am 01:17 AM
TocheckifaniPhoneisunlocked,1)gotoSettings>Cellular>CellularDataOptionsandlookforlabelslike“Unlocked”or“NoSIMrestrictions,”2)insertadifferentcarrier’sactiveSIMcardandseeifthephoneacceptsit,3)usetheIMEInumberononlinetoolslikeIMEI.infotocheckunlo
 BiAn Exchange mobile phone installation official v2.105.8 Android version update package
Jul 22, 2025 pm 10:06 PM
BiAn Exchange mobile phone installation official v2.105.8 Android version update package
Jul 22, 2025 pm 10:06 PM
1. Ensure the network stability and sufficient storage space of the device, and download it only through the official website; 2. Enter the official website in the mobile browser, find the download page and select the Android version, and download the v2.105.8 installation file with .apk as the suffix; 3. After the download is completed, enable the "Allow applications from this source" permission and click on the file to complete the installation; 4. Do not download through unofficial links, update the application version regularly, and pay attention to checking the environment security when logging in; 5. It is recommended to collect the official website download page for subsequent updates, and set up in-app security functions to ensure the security of digital assets.
 How to check iPhone trade-in value
Jul 13, 2025 am 01:13 AM
How to check iPhone trade-in value
Jul 13, 2025 am 01:13 AM
Determining the depreciation value of iPhone requires multiple factors and comparing different platforms. 2. The first choice is Apple's official replacement plan, which has a simple and transparent process, but the final valuation must be based on the actual condition of the equipment. 3. Third-party websites such as Gazelle, Swappa, etc. may provide higher quotations, but you need to pay attention to describing the real situation and avoiding the charging trap. 4. The core factors affecting value include model and storage capacity, equipment status, operator lock status, etc. Small problems may also affect the quotation. 5. If you pursue higher returns, you can choose to sell privately, but you need to weigh the time cost and transaction risks.
 How to download Binance on Apple mobile phone Android version Binance security portal
Jul 17, 2025 pm 04:30 PM
How to download Binance on Apple mobile phone Android version Binance security portal
Jul 17, 2025 pm 04:30 PM
Apple mobile phone users can access Binance by switching the App Store area or using the official web version. 1. Switch to Apple ID not in mainland China to log in to the App Store to download the app directly; 2. Use a mobile browser to access the Binance official website and trade without downloading the app. Android users should download the application through the official website and avoid unofficial channels to ensure security. After registering an account, you need to enable two-factor authentication (2FA) immediately to improve security.
 How to buy stablecoins for Apple phones? Where to buy stablecoins for Apple phones?
Jul 24, 2025 pm 09:18 PM
How to buy stablecoins for Apple phones? Where to buy stablecoins for Apple phones?
Jul 24, 2025 pm 09:18 PM
Purchase USDT and other stablecoins on Apple phones, you must download the compliant exchange app through the overseas Apple ID and complete the authentication and conduct transactions. The specific steps are as follows: 1. Use Apple ID in the non-mainland region to log in to the App Store; 2. Download recommended platforms such as OKX, Binance, Huobi (HTX), Gate.io or KuCoin; 3. Complete registration and identity authentication (KYC); 4. Enter the "Buy Coin" or "C2C/P2P Transaction" page to select USDT; 5. Filter merchants according to the payment method and place orders; 6. Pay through Alipay, WeChat or bank card and confirm transactions; 7. Wait for the merchant to put the coins into the account, and the entire process is completed.
 How to use the Files app on iPhone
Jul 19, 2025 am 01:48 AM
How to use the Files app on iPhone
Jul 19, 2025 am 01:48 AM
Using the iPhone's file app for file management is very simple and suitable for daily tasks. 1. Organize files and folders: Folders can be created through the "New Folder" function, and supports renaming, moving or copying files. They can also be sorted by name, date, etc. 2. Access iCloud and other cloud services: You can connect to iCloudDrive, GoogleDrive, Dropbox, etc., manage the displayed services through "Browse>Location>Edit", and directly save files to cloud storage. 3. Open and share files from other applications: Select the application to open the file through the share icon at the bottom, or share files through email, message or AirDrop. In short, although its functions are limited, its basic
 Forgot iPhone passcode
Jul 26, 2025 am 09:53 AM
Forgot iPhone passcode
Jul 26, 2025 am 09:53 AM
If you forget your iPhone password, you can try the following methods: 1. Use iTunes/Finder to enter recovery mode to restore the device (must be connected to the computer); 2. If you enable "Find My iPhone", you can erase the device through iCloud; 3. Contact Apple customer service for assistance (need to provide a purchase certificate). The first two of the above methods will clear the data. It is recommended to backup regularly in the future and enable the search function.





