 Mobile Game Tutorial
Mobile Game Tutorial
 Mobile Game Guide
Mobile Game Guide
 How to access DeepSeekapi - DeepSeekapi access call tutorial
How to access DeepSeekapi - DeepSeekapi access call tutorial
How to access DeepSeekapi - DeepSeekapi access call tutorial
Mar 12, 2025 pm 12:24 PMDetailed explanation of DeepSeek API access and call: Quick guide
This article will provide you with detailed instructions on how to access and call the DeepSeek API, helping you easily use powerful AI models.

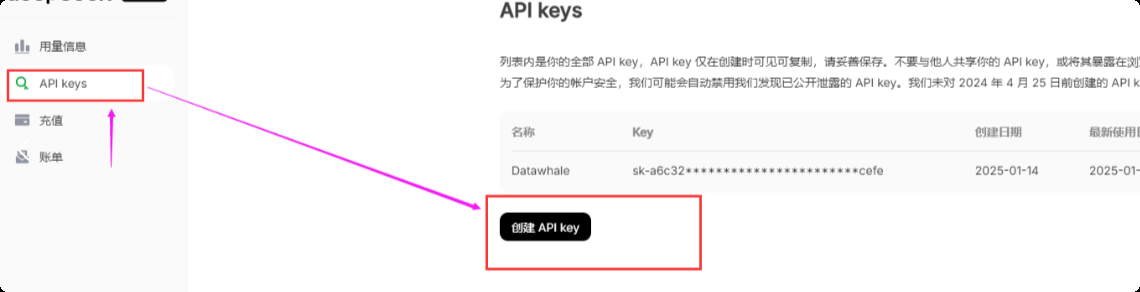
Step 1: Obtain the API key
- Visit the DeepSeek official website and click on the "Open Platform" in the upper right corner.

You will get a certain number of free tokens (for metering API usage). In the menu on the left, click "API Keys" and then click "Create API key".
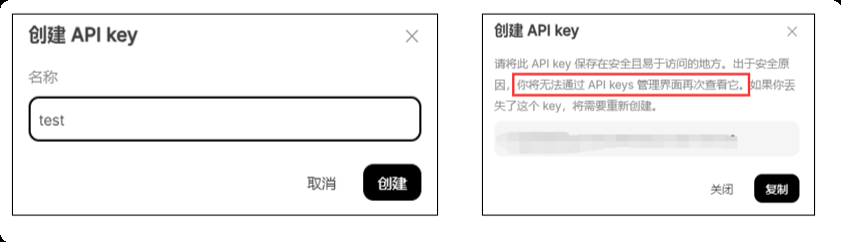
Name your API key (for example, "test") and copy the generated key immediately. Be sure to save this key properly as it will only be displayed once.
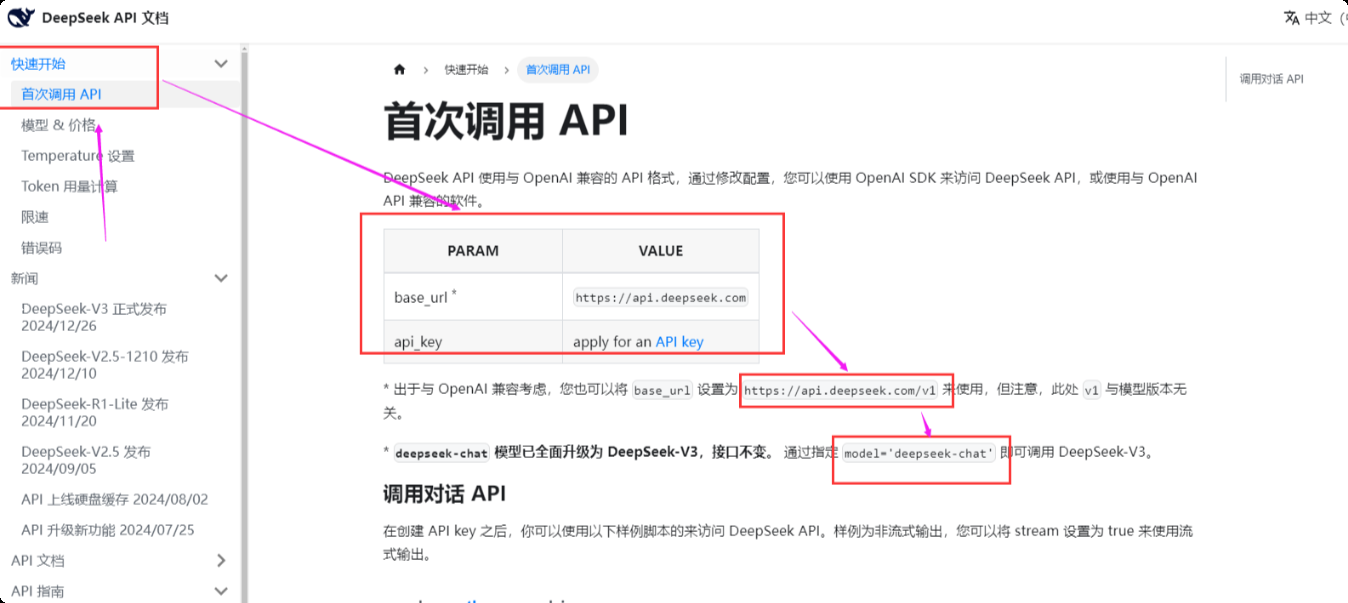
Step 2: Get base_url and chat_model
- In the Quick Start section of the DeepSeek API documentation, find
base_urlandchat_modelparameters. The acquisition methods of other platforms are similar.
Step 3: Configure model parameters
For security reasons, it is recommended to store the API key in environment variables rather than writing directly into the code. The following two methods are provided:
Method 1: The terminal temporarily sets environment variables (only valid in the current terminal session)
Enter the following command in the terminal to add your API key to the environment variable (replace YOUR_API_KEY with your actual key):
export API_KEY="YOUR_API_KEY"
Method 2: Create .env file (recommended)
- Create a file named
.env. - Add the following in the
.envfile, replacingYOUR_API_KEYwith your actual key:
<code>API_KEY="YOUR_API_KEY"</code>
In Python code, use the python-dotenv library to read environment variables:
from dotenv import load_dotenv
import os
load_dotenv() # Load the .env file api_key = os.getenv("API_KEY")
Step 4: Create a client
Create a DeepSeek client using base_url and api_key . (The specific client creation method depends on the library you are using)
Step 5: Test API calls
Here is a simple Python code example for testing API connections:
# ... (Previous code, including client creation) ...
response = client.chat(model=chat_model, messages=[{"role": "user", "content": "Hello"}])
print(response)
If everything is configured correctly, you will receive a reply from the model. If an error occurs, check that your API key and configuration are correct.
For more details, please refer to the official DeepSeek document. Original link (please replace it with the actual link)
The above is the detailed content of How to access DeepSeekapi - DeepSeekapi access call tutorial. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 What is Ethereum? What are the ways to obtain Ethereum ETH?
Jul 31, 2025 pm 11:00 PM
What is Ethereum? What are the ways to obtain Ethereum ETH?
Jul 31, 2025 pm 11:00 PM
Ethereum is a decentralized application platform based on smart contracts, and its native token ETH can be obtained in a variety of ways. 1. Register an account through centralized platforms such as Binance and Ouyiok, complete KYC certification and purchase ETH with stablecoins; 2. Connect to digital storage through decentralized platforms, and directly exchange ETH with stablecoins or other tokens; 3. Participate in network pledge, and you can choose independent pledge (requires 32 ETH), liquid pledge services or one-click pledge on the centralized platform to obtain rewards; 4. Earn ETH by providing services to Web3 projects, completing tasks or obtaining airdrops. It is recommended that beginners start from mainstream centralized platforms, gradually transition to decentralized methods, and always attach importance to asset security and independent research, to
 Ethena treasury strategy: the rise of the third empire of stablecoin
Jul 30, 2025 pm 08:12 PM
Ethena treasury strategy: the rise of the third empire of stablecoin
Jul 30, 2025 pm 08:12 PM
The real use of battle royale in the dual currency system has not yet happened. Conclusion In August 2023, the MakerDAO ecological lending protocol Spark gave an annualized return of $DAI8%. Then Sun Chi entered in batches, investing a total of 230,000 $stETH, accounting for more than 15% of Spark's deposits, forcing MakerDAO to make an emergency proposal to lower the interest rate to 5%. MakerDAO's original intention was to "subsidize" the usage rate of $DAI, almost becoming Justin Sun's Solo Yield. July 2025, Ethe
 What is Binance Treehouse (TREE Coin)? Overview of the upcoming Treehouse project, analysis of token economy and future development
Jul 30, 2025 pm 10:03 PM
What is Binance Treehouse (TREE Coin)? Overview of the upcoming Treehouse project, analysis of token economy and future development
Jul 30, 2025 pm 10:03 PM
What is Treehouse(TREE)? How does Treehouse (TREE) work? Treehouse Products tETHDOR - Decentralized Quotation Rate GoNuts Points System Treehouse Highlights TREE Tokens and Token Economics Overview of the Third Quarter of 2025 Roadmap Development Team, Investors and Partners Treehouse Founding Team Investment Fund Partner Summary As DeFi continues to expand, the demand for fixed income products is growing, and its role is similar to the role of bonds in traditional financial markets. However, building on blockchain
 Ethereum (ETH) NFT sold nearly $160 million in seven days, and lenders launched unsecured crypto loans with World ID
Jul 30, 2025 pm 10:06 PM
Ethereum (ETH) NFT sold nearly $160 million in seven days, and lenders launched unsecured crypto loans with World ID
Jul 30, 2025 pm 10:06 PM
Table of Contents Crypto Market Panoramic Nugget Popular Token VINEVine (114.79%, Circular Market Value of US$144 million) ZORAZora (16.46%, Circular Market Value of US$290 million) NAVXNAVIProtocol (10.36%, Circular Market Value of US$35.7624 million) Alpha interprets the NFT sales on Ethereum chain in the past seven days, and CryptoPunks ranked first in the decentralized prover network Succinct launched the Succinct Foundation, which may be the token TGE
 Solana and the founders of Base Coin start a debate: the content on Zora has 'basic value'
Jul 30, 2025 pm 09:24 PM
Solana and the founders of Base Coin start a debate: the content on Zora has 'basic value'
Jul 30, 2025 pm 09:24 PM
A verbal battle about the value of "creator tokens" swept across the crypto social circle. Base and Solana's two major public chain helmsmans had a rare head-on confrontation, and a fierce debate around ZORA and Pump.fun instantly ignited the discussion craze on CryptoTwitter. Where did this gunpowder-filled confrontation come from? Let's find out. Controversy broke out: The fuse of Sterling Crispin's attack on Zora was DelComplex researcher Sterling Crispin publicly bombarded Zora on social platforms. Zora is a social protocol on the Base chain, focusing on tokenizing user homepage and content
 What is Zircuit (ZRC currency)? How to operate? ZRC project overview, token economy and prospect analysis
Jul 30, 2025 pm 09:15 PM
What is Zircuit (ZRC currency)? How to operate? ZRC project overview, token economy and prospect analysis
Jul 30, 2025 pm 09:15 PM
Directory What is Zircuit How to operate Zircuit Main features of Zircuit Hybrid architecture AI security EVM compatibility security Native bridge Zircuit points Zircuit staking What is Zircuit Token (ZRC) Zircuit (ZRC) Coin Price Prediction How to buy ZRC Coin? Conclusion In recent years, the niche market of the Layer2 blockchain platform that provides services to the Ethereum (ETH) Layer1 network has flourished, mainly due to network congestion, high handling fees and poor scalability. Many of these platforms use up-volume technology, multiple transaction batches processed off-chain
 python connect to sql server pyodbc example
Jul 30, 2025 am 02:53 AM
python connect to sql server pyodbc example
Jul 30, 2025 am 02:53 AM
Install pyodbc: Use the pipinstallpyodbc command to install the library; 2. Connect SQLServer: Use the connection string containing DRIVER, SERVER, DATABASE, UID/PWD or Trusted_Connection through the pyodbc.connect() method, and support SQL authentication or Windows authentication respectively; 3. Check the installed driver: Run pyodbc.drivers() and filter the driver name containing 'SQLServer' to ensure that the correct driver name is used such as 'ODBCDriver17 for SQLServer'; 4. Key parameters of the connection string
 How can we avoid being a buyer when trading coins? Beware of risks coming
Jul 30, 2025 pm 08:06 PM
How can we avoid being a buyer when trading coins? Beware of risks coming
Jul 30, 2025 pm 08:06 PM
To avoid taking over at high prices of currency speculation, it is necessary to establish a three-in-one defense system of market awareness, risk identification and defense strategy: 1. Identify signals such as social media surge at the end of the bull market, plunge after the surge in the new currency, and giant whale reduction. In the early stage of the bear market, use the position pyramid rules and dynamic stop loss; 2. Build a triple filter for information grading (strategy/tactics/noise), technical verification (moving moving averages and RSI, deep data), emotional isolation (three consecutive losses and stops, and pulling the network cable); 3. Create three-layer defense of rules (big whale tracking, policy-sensitive positions), tool layer (on-chain data monitoring, hedging tools), and system layer (barbell strategy, USDT reserves); 4. Beware of celebrity effects (such as LIBRA coins), policy changes, liquidity crisis and other scenarios, and pass contract verification and position verification and





