 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 What is the role of Debian Apache logs on website security
What is the role of Debian Apache logs on website security
What is the role of Debian Apache logs on website security
Apr 12, 2025 pm 11:27 PM
Apache logs under the Debian system are crucial to website security, and their roles are reflected in the following aspects:
1. Security incident tracking and prevention
Apache log records all website access requests, including IP address, access time, request resource (URL), and HTTP status code. By analyzing these logs, you can:
- Identify malicious activity: Discover suspicious access patterns such as signs of large numbers of requests in a short period of time, frequent login failure attempts (brute force), SQL injection or cross-site scripting attacks (XSS).
- Tracking the source of the attack: locate the attacker's IP address to provide a basis for taking defensive measures.
- Analyze attack patterns: Study historical log data and identify common attack patterns and trends to improve security policies and defense mechanisms.
2. System monitoring and performance optimization
In addition to security monitoring, Apache logs are also used for:
- Resource usage monitoring: Track the consumption of server resources (CPU, memory, bandwidth), help administrators optimize server configuration and improve performance.
- Access traffic analysis: Understand user access habits and traffic patterns, and provide data support for the formulation of load balancing policies.
- Troubleshooting: When a website fails, the log can provide detailed error information and request paths, which facilitates quick location and resolution of problems.
III. Compliance and Audit
Apache logging helps:
- Meet compliance requirements: Many industry standards and regulations require websites to keep access logs, which Apache logs can meet.
- Provide audit evidence: When a security incident occurs, the log can be used as important evidence for investigation and analysis.
4. Automated response
Scripts can be written to automatically analyze Apache logs and act on preset rules, such as:
- Automatic alarm: When a security event is detected, an alarm is automatically sent to notify the administrator.
- Automatic block: Automatic block malicious IP addresses.
5. Important things to note
- Log security: Log files must be properly protected from unauthorized access and tampering.
- Regular backup: Back up log files regularly to prevent data loss.
- Data compliance: Comply with relevant laws and regulations, and properly handle and protect user data.
In short, Debian Apache logs are an important part of website security and operation and maintenance management. Effective utilization of log information can significantly improve website security and optimize system performance.
The above is the detailed content of What is the role of Debian Apache logs on website security. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
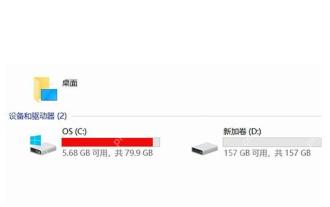 How to expand the capacity of the c disk if it is too small? 5 solutions for small capacity c disk expansion
May 22, 2025 pm 09:15 PM
How to expand the capacity of the c disk if it is too small? 5 solutions for small capacity c disk expansion
May 22, 2025 pm 09:15 PM
C drive can expand capacity in five ways: 1. Use Windows disk management tools to expand the volume, but there must be unallocated space; 2. Use third-party software such as EaseUS or AOMEI to adjust the partition size; 3. Use Diskpart command line tools to expand the C drive, suitable for users who are familiar with the command line; 4. Repartition and format the hard disk, but it will cause data loss and data needs to be backed up; 5. Use external storage devices as C drive expansion, transfer folders through symbolic links or modification of the registry.
 How to execute php code after writing php code? Several common ways to execute php code
May 23, 2025 pm 08:33 PM
How to execute php code after writing php code? Several common ways to execute php code
May 23, 2025 pm 08:33 PM
PHP code can be executed in many ways: 1. Use the command line to directly enter the "php file name" to execute the script; 2. Put the file into the document root directory and access it through the browser through the web server; 3. Run it in the IDE and use the built-in debugging tool; 4. Use the online PHP sandbox or code execution platform for testing.
 How to update Debian Tomcat
May 28, 2025 pm 04:54 PM
How to update Debian Tomcat
May 28, 2025 pm 04:54 PM
Updating the Tomcat version in the Debian system generally includes the following process: Before performing the update operation, be sure to do a complete backup of the existing Tomcat environment. This covers the /opt/tomcat folder and its related configuration documents, such as server.xml, context.xml, and web.xml. The backup task can be completed through the following command: sudocp-r/opt/tomcat/opt/tomcat_backup Get the new version Tomcat Go to ApacheTomcat's official website to download the latest version. According to your Debian system
 How to create a SQLite database in Python?
May 23, 2025 pm 10:36 PM
How to create a SQLite database in Python?
May 23, 2025 pm 10:36 PM
Create a SQLite database in Python using the sqlite3 module. The steps are as follows: 1. Connect to the database, 2. Create a cursor object, 3. Create a table, 4. Submit a transaction, 5. Close the connection. This is not only simple and easy to do, but also includes optimizations and considerations such as using indexes and batch operations to improve performance.
 What does java middleware mean? Definition and typical applications of middleware
May 28, 2025 pm 05:51 PM
What does java middleware mean? Definition and typical applications of middleware
May 28, 2025 pm 05:51 PM
Java middleware is a software that connects operating systems and application software, providing general services to help developers focus on business logic. Typical applications include: 1. Web server (such as Tomcat and Jetty), which handles HTTP requests; 2. Message queue (such as Kafka and RabbitMQ), which handles asynchronous communication; 3. Transaction management (such as SpringTransaction), which ensures data consistency; 4. ORM framework (such as Hibernate and MyBatis), which simplifies database operations.
 What are the Debian Hadoop monitoring tools?
May 23, 2025 pm 09:57 PM
What are the Debian Hadoop monitoring tools?
May 23, 2025 pm 09:57 PM
There are many methods and tools for monitoring Hadoop clusters on Debian systems. The following are some commonly used monitoring tools and their usage methods: Hadoop's own monitoring tool HadoopAdminUI: Access the HadoopAdminUI interface through a browser to intuitively understand the cluster status and resource utilization. HadoopResourceManager: Access the ResourceManager WebUI (usually http://ResourceManager-IP:8088) to monitor cluster resource usage and job status. Hadoop
 Efficient operation method for batch stopping Docker containers
May 19, 2025 pm 09:03 PM
Efficient operation method for batch stopping Docker containers
May 19, 2025 pm 09:03 PM
An efficient way to batch stop a Docker container includes using basic commands and tools. 1. Use the dockerstop$(dockerps-q) command and adjust the timeout time, such as dockerstop-t30$(dockerps-q). 2. Use dockerps filtering options, such as dockerstop$(dockerps-q--filter"label=app=web"). 3. Use the DockerCompose command docker-composedown. 4. Write scripts to stop containers in order, such as stopping db, app and web containers.
 What are the SEO optimization techniques for Debian Apache2?
May 28, 2025 pm 05:03 PM
What are the SEO optimization techniques for Debian Apache2?
May 28, 2025 pm 05:03 PM
DebianApache2's SEO optimization skills cover multiple levels. Here are some key methods: Keyword research: Use tools (such as keyword magic tools) to mine the core and auxiliary keywords of the page. High-quality content creation: produce valuable and original content, and the content needs to be conducted in-depth research to ensure smooth language and clear format. Content layout and structure optimization: Use titles and subtitles to guide reading. Write concise and clear paragraphs and sentences. Use the list to display key information. Combining multimedia such as pictures and videos to enhance expression. The blank design improves the readability of text. Technical level SEO improvement: robots.txt file: Specifies the access rights of search engine crawlers. Accelerate web page loading: optimized with the help of caching mechanism and Apache configuration





