 Computer Tutorials
Computer Tutorials
 Computer Knowledge
Computer Knowledge
 How to change WeChat real-name authentication How to change WeChat real-name authentication
How to change WeChat real-name authentication How to change WeChat real-name authentication
How to change WeChat real-name authentication How to change WeChat real-name authentication
Feb 22, 2024 pm 03:34 PMphp editor Strawberry will introduce you in detail the method and location of changing WeChat real-name authentication. WeChat real-name authentication is an important step in ensuring account security. If you need to change your real-name information, you need to do so in WeChat settings. This article will explain the steps for changing WeChat real-name authentication and help you better manage your account information.
You can log out first on the WeChat account name change interface, and then perform real-name authentication again.
Tutorial applies
Model: iPhone 13
System: iOS 15.2
Version: WeChat 8.0.16
Analysis
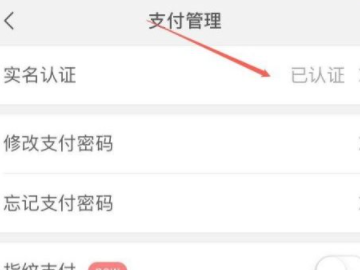
1After entering the My interface on WeChat, click Pay.
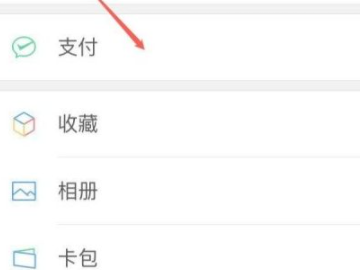
2Click on the three small dots in the upper right corner.
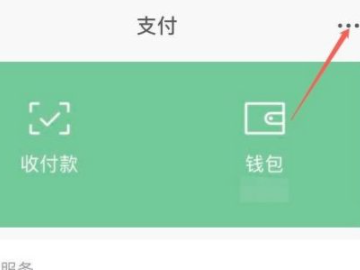
3Click on the real-name authentication option.

4Click below to change the account name.

5Click again to confirm the logout.

6Choose the logout method and log out.
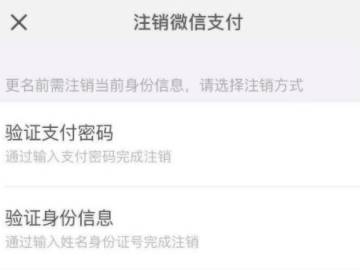
7After logging out successfully, click Confirm.
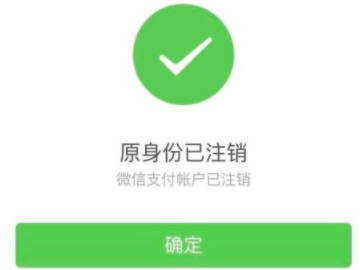
8At this point, return to real-name authentication and perform real-name authentication again.
Supplement: What is WeChat real-name authentication
1WeChat real-name authentication is also the WeChat real-name system. It is a specific measure for the supervision of real identity information on the Internet in my country. It is based on the principle of back-end real-name and front-end voluntary, including Weibo, Tieba, etc. Real-name system, for which supervision, management and law enforcement will be strengthened.

Summary/Notes
WeChat real-name authentication cannot be changed directly. You can only log out the previous real-name authentication first.
The above is the detailed content of How to change WeChat real-name authentication How to change WeChat real-name authentication. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to use PHP to build social sharing functions PHP sharing interface integration practice
Jul 25, 2025 pm 08:51 PM
How to use PHP to build social sharing functions PHP sharing interface integration practice
Jul 25, 2025 pm 08:51 PM
The core method of building social sharing functions in PHP is to dynamically generate sharing links that meet the requirements of each platform. 1. First get the current page or specified URL and article information; 2. Use urlencode to encode the parameters; 3. Splice and generate sharing links according to the protocols of each platform; 4. Display links on the front end for users to click and share; 5. Dynamically generate OG tags on the page to optimize sharing content display; 6. Be sure to escape user input to prevent XSS attacks. This method does not require complex authentication, has low maintenance costs, and is suitable for most content sharing needs.
 How to trade stablecoins_A full flow diagram for beginners buying and selling
Jul 18, 2025 am 06:00 AM
How to trade stablecoins_A full flow diagram for beginners buying and selling
Jul 18, 2025 am 06:00 AM
The stablecoin trading process includes the steps of registering an exchange, completing certification, buying or selling. First, choose a trusted exchange such as Binance, OKX, etc., and then complete KYC identity authentication, and then buy stablecoins through fiat currency recharge or OTC transactions. You can also transfer the stablecoins to the fund account and sell them through P2P transactions and withdraw them to the bank card or Alipay. When operating, you need to pay attention to choosing a regulated platform, confirm transaction security and handling fees.
 PHP realizes commodity inventory management and monetization PHP inventory synchronization and alarm mechanism
Jul 25, 2025 pm 08:30 PM
PHP realizes commodity inventory management and monetization PHP inventory synchronization and alarm mechanism
Jul 25, 2025 pm 08:30 PM
PHP ensures inventory deduction atomicity through database transactions and FORUPDATE row locks to prevent high concurrent overselling; 2. Multi-platform inventory consistency depends on centralized management and event-driven synchronization, combining API/Webhook notifications and message queues to ensure reliable data transmission; 3. The alarm mechanism should set low inventory, zero/negative inventory, unsalable sales, replenishment cycles and abnormal fluctuations strategies in different scenarios, and select DingTalk, SMS or Email Responsible Persons according to the urgency, and the alarm information must be complete and clear to achieve business adaptation and rapid response.
 How to download the official Bitcoin app? Bitcoin App Use Guide
Jul 22, 2025 pm 11:54 PM
How to download the official Bitcoin app? Bitcoin App Use Guide
Jul 22, 2025 pm 11:54 PM
Bitcoin does not have an official app, and users mainly trade and manage them through third-party exchanges or account apps. 1. Binance has comprehensive functions and is suitable for all kinds of traders; 2. OKX provides integrated trading and Web3 accounts; 3. Huobi (HTX) is stable and reliable in the Asian market; 4. Gate.io is known for its rich currency; 5. KuCoin has diverse currencies and active communities; 6. Bybit is known for its derivatives trading. When downloading, you should visit the official website, scan the QR code, complete the installation according to the system, and set up security measures such as two-factor verification to ensure the security of the account.
 How to use PHP to build a payment system to monetize PHP payment interface docking process
Jul 25, 2025 pm 06:24 PM
How to use PHP to build a payment system to monetize PHP payment interface docking process
Jul 25, 2025 pm 06:24 PM
Choose a payment platform based on user portrait. WeChat Pay is suitable for users in the WeChat ecosystem, and Alipay is suitable for mature consumer groups and PC-side large-scale payments; 2. Registering a merchant account to obtain AppID, MCHID, API keys and other qualifications is the prerequisite; 3. Using the official PHPSDK integrated interface can simplify development and improve security; 4. The PHP backend generates orders and initiates prepayment requests, and the front end calls for payment based on the returned data; 5. Asynchronous callbacks are the final basis for successful payment, and signatures, IP whitelists, SSL encryption transmission must be verified and idempotence must be realized to prevent repeated processing; 6. Timeout orders are closed through timed tasks, refunds must be called to the API and handled multiple states, reconciliation needs to be regularly compared with the platform flow and system orders to ensure the consistency of funds, and the entire flow
 How to buy stablecoins for Apple phones? Where to buy stablecoins for Apple phones?
Jul 24, 2025 pm 09:18 PM
How to buy stablecoins for Apple phones? Where to buy stablecoins for Apple phones?
Jul 24, 2025 pm 09:18 PM
Purchase USDT and other stablecoins on Apple phones, you must download the compliant exchange app through the overseas Apple ID and complete the authentication and conduct transactions. The specific steps are as follows: 1. Use Apple ID in the non-mainland region to log in to the App Store; 2. Download recommended platforms such as OKX, Binance, Huobi (HTX), Gate.io or KuCoin; 3. Complete registration and identity authentication (KYC); 4. Enter the "Buy Coin" or "C2C/P2P Transaction" page to select USDT; 5. Filter merchants according to the payment method and place orders; 6. Pay through Alipay, WeChat or bank card and confirm transactions; 7. Wait for the merchant to put the coins into the account, and the entire process is completed.
 How to build a content payment platform through PHP How to implement PHP paid reading system
Jul 25, 2025 pm 06:30 PM
How to build a content payment platform through PHP How to implement PHP paid reading system
Jul 25, 2025 pm 06:30 PM
To build a PHP content payment platform, it is necessary to build a user management, content management, payment and permission control system. First, establish a user authentication system and use JWT to achieve lightweight authentication; second, design the backend management interface and database fields to manage paid content; third, integrate Alipay or WeChat payment and ensure process security; fourth, control user access rights through session or cookies. Choosing the Laravel framework can improve development efficiency, use watermarks and user management to prevent content theft, optimize performance requires coordinated improvement of code, database, cache and server configuration, and clear policies must be formulated and malicious behaviors must be prevented.
 How to use the Files app on iPhone
Jul 19, 2025 am 01:48 AM
How to use the Files app on iPhone
Jul 19, 2025 am 01:48 AM
Using the iPhone's file app for file management is very simple and suitable for daily tasks. 1. Organize files and folders: Folders can be created through the "New Folder" function, and supports renaming, moving or copying files. They can also be sorted by name, date, etc. 2. Access iCloud and other cloud services: You can connect to iCloudDrive, GoogleDrive, Dropbox, etc., manage the displayed services through "Browse>Location>Edit", and directly save files to cloud storage. 3. Open and share files from other applications: Select the application to open the file through the share icon at the bottom, or share files through email, message or AirDrop. In short, although its functions are limited, its basic





