Found a total of 10000 related content
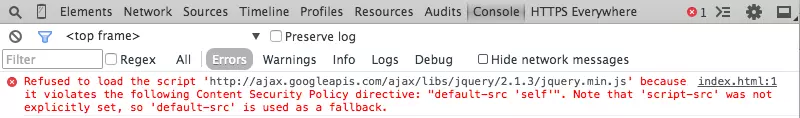
Improving Web Security with the Content Security Policy
Article Introduction:Content Security Policy (CSP): A Comprehensive Guide to Web Security
Content Security Policy (CSP) is a crucial security mechanism safeguarding websites against content injection attacks, primarily Cross-Site Scripting (XSS). This declarative policy
2025-02-20
comment 0
1091

Spring Security Basic Guide
Article Introduction:Spring Security is one of the most robust and versatile modules in the Spring framework, designed to provide complete security for Java applications. With it, you can configure authentication, authorization and other security practices.
To understand honey
2024-11-01
comment 0
1104



How to ensure FetchDebian security
Article Introduction:FetchDebian (usually refers to the process of obtaining software packages from a Debian repository through the APT package manager) does not directly provide security guarantees, but it relies on the security mechanism and update process of the Debian distribution body. Here are detailed instructions on how to ensure system security through FetchDebian: Debian's security update mechanism is regularly updated: Debian projects will regularly release security updates and patches to fix known security vulnerabilities and improve system stability. Users can automatically update the system through APT commands to ensure their software
2025-04-13
comment 0
549

What is operation and maintenance security?
Article Introduction:This article examines DevSecOps, integrating security into the software development lifecycle. It details a DevOps security engineer's multifaceted role, encompassing security architecture, automation, vulnerability management, and incident response
2025-03-05
comment 0
456

MongoDB: Security, Performance, and Stability
Article Introduction:MongoDB excels in security, performance and stability. 1) Security is achieved through authentication, authorization, data encryption and network security. 2) Performance optimization depends on indexing, query optimization and hardware configuration. 3) Stability is guaranteed through data persistence, replication sets and sharding.
2025-04-10
comment 0
762

What is operation and maintenance security?
Article Introduction:DevOps enhances operational security by automating security checks within CI/CD pipelines, utilizing Infrastructure as Code for improved control, and fostering collaboration between development and security teams. This approach accelerates vulnerabi
2025-03-05
comment 0
476

TikTok Has a New Security Checkup Dashboard
Article Introduction:TikTok enhances user security with a new built-in Security Checkup tool. This dashboard helps users monitor their account's security status and provides step-by-step instructions to improve their settings.
Accessing TikTok's Security Checkup
To acces
2025-03-21
comment 0
788

Windows Security blank screen
Article Introduction:When Windows Security displays blank pages, it is usually caused by system component exceptions or settings conflicts. 1. Check and uninstall third-party security software because it may block Windows Security; 2. Use sfc/scannow and DISM commands to repair system files; 3. Reset Windows Security application through "Settings"; 4. Check whether the Group Policy settings disable Microsoft Defender antivirus function. Follow the above steps to check in turn, and in most cases the problem can be solved.
2025-07-08
comment 0
469

How to ensure the security of H5 page production
Article Introduction:There are many security threats in H5 page production, including XSS, CSRF, SQL injection and data breaches. To ensure the security of H5 pages, basic security measures must be taken, including input verification, output escaping, use of HTTPS and security frameworks. In addition, more advanced security policies need to be considered, such as authentication and authorization, security audits and regular security scans, and continuous learning and updating security knowledge and continuous improvement of security policies.
2025-04-06
comment 0
863

Main work of operation and maintenance security
Article Introduction:This article details operational and maintenance (O&M) security, emphasizing vulnerability management, access control, security monitoring, data protection, and physical security. Key responsibilities and mitigation strategies, including proacti
2025-03-05
comment 0
442

NSEML-: Fortinet Network Security Expert Practice 4
Article Introduction:NSE7_PBC-7.2: Fortinet Network Security Expert Practice 2024
https://www.udemy.com/course/nse7_pbc-72-fortinet-network-security-expert-practice/?couponCode=AEAE51CC6705B6548825
NSE7_PBC-6.4: Fortinet Network Security Expert Practice 2024
htt
2024-11-30
comment 0
797

NSEAZ-: Fortinet Network Security Expert Practice 4
Article Introduction:NSE5_FAZ-7.0: Fortinet Network Security Expert Practice 2024
https://www.udemy.com/course/nse5_faz-70-fortinet-network-security-expert-practice/?couponCode=841346FA19B10C78882A
NSE5_EDR-5.0: Fortinet Network Security Expert Practice 2024
htt
2024-11-16
comment 0
793

IIS's Capabilities: Performance and Security
Article Introduction:How does IIS perform in terms of performance and security? IIS is optimized in terms of performance by enabling compression, tuning application pool settings and performance monitoring; in terms of security, it is protected by enabling HTTPS, restricting IP access and security monitoring, but it also faces some challenges.
2025-04-27
comment 0
572

Strengthening Linux Security by Auditing with OpenSCAP
Article Introduction:introduction
In today's complex digital environments, cyber threats are increasing, and ensuring the security of Linux systems is crucial. Security audits play a key role in identifying and mitigating vulnerabilities, protecting sensitive data, and maintaining regulatory compliance. OpenSCAP is a powerful tool that can help with this job. This guide will dive into the details of using OpenSCAP for Linux security audits, including its capabilities, implementations, and best practices.
Understand security audits
Security audit is a process of systematic analysis of system security measures to identify weaknesses, assess risks, and ensure compliance with security policies and standards. In Linux environments, security auditing becomes indispensable due to the diversity of architecture and configuration. Common vulnerabilities, such as errors
2025-03-09
comment 0
1138

How to Integrate Spring Security CORS Filter?
Article Introduction:Spring Security CORS Filter IntegrationSpring Security requires CORS configuration to handle cross-origin requests. To address this issue...
2024-11-01
comment 0
494
















