 Computer Tutorials
Computer Tutorials
 System Installation
System Installation
 How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AMWhen the U disk is write-protected, the storage device will not be able to write data, affecting our work and life. If you encounter a U disk write-protection situation, this tutorial will provide you with several simple and effective solutions to help you quickly remove the write protection and restore the normal use of the U disk. PHP editor Baicao carefully summarized these methods to ensure that they are practical and easy to operate. By reading this article, you will be able to easily solve the USB flash drive write protection problem and restore the data access permissions of the USB flash drive.

Tool materials:
System version: Windows 10 20H2, macOS Big Sur 11.2.3
Brand model: SanDisk Ultra Flair USB 3.0 flash drive, Kingston DataTraveler 100 G3 USB 3.0 flash drive
Software version: DiskGenius 5.4.2.1239, ChipGenius 4.19.1225
1. Check the physical write protection switch of the U disk
Some U disks are designed with a physical write protection switch, which can be turned on and off by flipping the switch position. If your USB flash drive has this switch, please confirm whether the switch is in the write-protected position. If so, flip it to the non-write-protected position to release the write protection.
2. Use Disk Manager to remove write protection
1. Under Windows system, right-click "This Computer" and select "Manage" to open the computer management interface.
2. Select "Disk Management" in the left menu, find the write-protected U disk, right-click the U disk partition, and select "Properties".
3. In the properties window, uncheck the "Read-only" option and click "OK" to remove the write protection.
3. Use third-party tools to remove write protection
1. Download and install professional U disk repair tools such as DiskGenius or ChipGenius.
2. Insert the write-protected USB flash drive, open the repair tool, and select the USB flash drive that needs to be repaired.
3. Find the "Eliminate USB device write protection" or similar option in the tool interface, click Execute, and wait for the repair to be completed to remove the write protection.
Content extension:
1. Back up U disk data regularly to avoid data loss due to write protection or other reasons.
2. Using high-quality brand U disks, such as SanDisk, Kingston, etc., can effectively reduce the occurrence of write protection and other problems.
3. Avoid frequently plugging and unplugging U disks between multiple devices, which may increase the risk of write protection and other problems.
4. If the above method cannot remove the write protection, it may be caused by damage to the U disk hardware. It is recommended to send it for repair or replace it with a new one.
Summary:
U disk write protection is a common problem. By checking the physical switch, using the system's own disk manager or third-party repair tools, most write protection problems can be solved has been solved. At the same time, developing good U disk usage habits and choosing high-quality brand products can also effectively prevent the occurrence of write protection problems.
The above is the detailed content of How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Navicat's recovery method for importing database backup files (such as .bak)
Jun 04, 2025 pm 06:51 PM
Navicat's recovery method for importing database backup files (such as .bak)
Jun 04, 2025 pm 06:51 PM
The method of using Navicat to restore .bak files is as follows: 1. Open Navicat and connect to the SQLServer instance. 2. Create a new database or select an existing database. 3. Enter and execute the RESTOREDATABASESQL statement in the query editor to ensure that the path and name are correct. 4. Pay attention to the use of database name, file path, WITHREPLACE and MOVE options to ensure successful recovery.
 Ouyi download tutorial Ouyi latest version download tutorial (full version)
Jun 18, 2025 pm 07:39 PM
Ouyi download tutorial Ouyi latest version download tutorial (full version)
Jun 18, 2025 pm 07:39 PM
As the world's leading cryptocurrency exchange, OKX provides a safe and reliable trading environment and a rich variety of digital assets. 1. Visit the official website www.okx.com to download the application; 2. Select the Android or iOS version according to the device; 3. Install the application and complete registration or login; 4. Enable two-factor verification to ensure account security. The platform supports spot trading, leveraged trading, contract trading, DeFi, OKX Earn financial management and NFT market.
 How to adjust mysql into Chinese interface? Easy to set the Chinese language environment of mysql
Jun 04, 2025 pm 06:36 PM
How to adjust mysql into Chinese interface? Easy to set the Chinese language environment of mysql
Jun 04, 2025 pm 06:36 PM
To tune MySQL into a Chinese interface, it can be implemented through MySQLWorkbench or command line tools. 1) In MySQLWorkbench, open "Preferences", select the "Appearance" tab, and then select "Chinese(Simplified)" in the "Language" drop-down menu, and restart. 2) When using command line tools, set the operating system locale variables, such as using "exportLANG=zh_CN.UTF-8" on Linux or macOS, and then run the mysql client.
 Yiou Exchange Download and Installation Pack okx Android Installation Pack
Jun 12, 2025 pm 10:21 PM
Yiou Exchange Download and Installation Pack okx Android Installation Pack
Jun 12, 2025 pm 10:21 PM
To download the OKX Android installation package, you must access it through the official website and click the "App Download" button to obtain it to avoid third-party platforms.
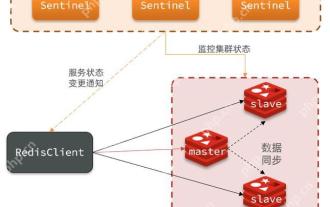 Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
The quick location and processing steps for Redis cluster node failure are as follows: 1. Confirm the fault: Use the CLUSTERNODES command to view the node status. If the fail is displayed, the node will fail. 2. Determine the cause: Check the network, hardware, and configuration. Common problems include memory limits exceeding. 3. Repair and restore: Take measures based on the reasons, such as restarting the service, replacing the hardware or modifying the configuration. 4. Notes: Ensure data consistency, select appropriate failover policies, and establish monitoring and alarm systems.
 How to modify table structure in phpMyAdmin? Adjust fields and types
Jun 04, 2025 pm 09:18 PM
How to modify table structure in phpMyAdmin? Adjust fields and types
Jun 04, 2025 pm 09:18 PM
The operation of modifying the table structure in phpMyAdmin mainly includes the following steps: 1. Enter the "Structure" page of the target database and table; 2. Click the "Change" button of the field to edit; 3. Modify the field name, type, length, whether it is allowed to be empty; 4. Adjust the field order or add new fields; 5. Confirm data compatibility and application layer logic before saving. When modifying, special attention should be paid to the compatibility of primary keys, index fields and existing data to avoid index failure or data loss. It is recommended to back up data before operation.
 Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Effective solutions to the problem of split brain in Redis cluster include: 1) Network configuration optimization to ensure connection stability; 2) Node monitoring and fault detection, real-time monitoring with tools; 3) Failover mechanism, setting high thresholds to avoid multiple master nodes; 4) Data consistency guarantee, using replication function to synchronize data; 5) Manual intervention and recovery, and manual processing if necessary.
 Huobi Online Entrance Huobi App Download Tutorial Latest Version
Jun 24, 2025 pm 05:45 PM
Huobi Online Entrance Huobi App Download Tutorial Latest Version
Jun 24, 2025 pm 05:45 PM
The latest version of Huobi App download tutorial is as follows: Step 1, visit Huobi official website, confirm the correctness of the URL and select the official website in the region; Step 2, find the app download portal, and select the Android version or iOS version according to the mobile operating system; Step 3, choose the download method, including scanning the QR code, directly downloading the installation package or jumping to the app store to download; Step 4, install the app. If it is the installation package, you need to allow the installation of applications from unknown sources. If it is an app store, click to install; Step 5, open the App to log in to the account, and if it is an account, you can register a new account if you don’t have an account. Frequently asked questions include: if the network is unstable, the system is upgraded or the old version is downloaded, the file is damaged, and the application store cannot be searched.





