 Operation and Maintenance
Operation and Maintenance
 Nginx
Nginx
 How Nginx implements access control configuration based on request source domain name
How Nginx implements access control configuration based on request source domain name
How Nginx implements access control configuration based on request source domain name
Nov 08, 2023 am 09:06 AM
How Nginx implements access control configuration based on the request source domain name requires specific code examples
Nginx is a high-performance web server software. It can not only be used as a static The file server can also be configured to achieve flexible access control. This article will introduce how to implement access control configuration based on the request source domain name through Nginx, and provide specific code examples.
The Nginx configuration file is usually located in /etc/nginx/nginx.conf. We can add relevant configurations to this file. Here is an example of a basic Nginx configuration file:
http {
server {
listen 80;
server_name example.com;
location / {
proxy_pass http://localhost:8000;
}
}
}In the above example, we listen to port 80 and forward all requests to the local port 8000. The server_name directive is used in this configuration to specify the domain name that accepts requests. By default, Nginx will accept requests from all domain names. If you want to implement access control configuration based on the domain name of the request source, you can use the if directive combined with $request_header to achieve this.
The following is an example:
http {
server {
listen 80;
if ($http_host ~* "^(www.)?example.com$") {
location / {
proxy_pass http://localhost:8000;
}
}
if ($http_host ~* "^(www.)?example2.com$") {
return 403;
}
}
}In the above example, we use two if instructions to implement access control configuration based on the request source domain name. In the first if block, we use the $http_host variable to match the example.com domain name and forward the request to the local port 8000. In the second if block, we also use the $http_host variable to match the example2.com domain name and return a 403 error.
It should be noted that using the if instruction in Nginx will cause performance losses. If possible, it is recommended to use regular expressions for domain name matching and use the location directive to achieve more efficient configuration.
In addition to using the if directive, Nginx also provides many other directives and modules for implementing more complex access control configurations, such as the ngx_http_access_module module, ngx_http_auth_basic_module module, etc. You can choose the appropriate configuration method according to actual needs.
To summarize, access control configuration based on the domain name of the request source can be implemented through Nginx. By using the if directive in combination with the $http_host variable in the configuration file, conditional judgment can be made based on the requested domain name, thereby achieving flexible access control. Of course, in order to ensure performance, it is recommended to choose an appropriate configuration method and combine it with other modules to achieve more complex control requirements.
The above is the detailed content of How Nginx implements access control configuration based on request source domain name. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Nginx error page configuration, beautify website failure prompts
Jul 04, 2023 pm 01:33 PM
Nginx error page configuration, beautify website failure prompts
Jul 04, 2023 pm 01:33 PM
Nginx error page configuration, beautify website fault prompts. During the operation of the website, it is inevitable to encounter server errors or other faults. These problems will cause users to be unable to access the website normally. In order to improve user experience and website image, we can configure Nginx error pages to beautify website failure prompts. This article will introduce how to customize the error page through Nginx's error page configuration function, and provide code examples as a reference. 1. Modify the Nginx configuration file. First, we need to open the Nginx configuration.
 How to use Vue for permission management and access control
Aug 02, 2023 pm 09:01 PM
How to use Vue for permission management and access control
Aug 02, 2023 pm 09:01 PM
How to use Vue for permission management and access control In modern web applications, permission management and access control is a critical feature. As a popular JavaScript framework, Vue provides a simple and flexible way to implement permission management and access control. This article will introduce how to use Vue to implement basic permission management and access control functions, and attach code examples. Defining Roles and Permissions Before you begin, you first need to define the roles and permissions in your application. A role is a specific set of permissions, and
 How to implement Nginx cross-origin resource sharing (CORS) configuration
Nov 08, 2023 pm 12:22 PM
How to implement Nginx cross-origin resource sharing (CORS) configuration
Nov 08, 2023 pm 12:22 PM
How to implement Nginx's cross-domain resource sharing (CORS) configuration requires specific code examples. With the popularity of front-end and back-end separation development, cross-domain resource sharing (CORS) issues have become a common challenge. In web development, due to the browser's same-origin policy restrictions, client-side JavaScript code can only request resources with the same domain name, protocol, and port as the page where it is located. However, in actual development, we often need to request resources from different domain names or different subdomains. At this time, you need to use CO
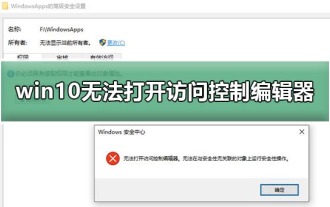 Access Control Editor cannot be opened in Win10
Jan 03, 2024 pm 10:05 PM
Access Control Editor cannot be opened in Win10
Jan 03, 2024 pm 10:05 PM
The inability to open the access control editor in win10 is an uncommon problem. This problem usually occurs in external hard drives and USB flash drives. In fact, the solution is very simple. Just open it in safe mode and take a look. Let’s take a look at the details below. tutorial. Win10 cannot open the access control editor 1. In the login interface, hold down shift, click the button, click 2.--, click 3. After restarting, press F5 to try to enter and see if you can enter. Articles related to win10 safe mode>>>How to enter win10 safe mode<<<>>>How to repair the system in win10 safe mode<<<
 Implementing Role-Based Access Control (RBAC): Using PHP and RBAC
Jun 20, 2023 pm 10:39 PM
Implementing Role-Based Access Control (RBAC): Using PHP and RBAC
Jun 20, 2023 pm 10:39 PM
With the popularity of Internet applications, we hope to protect data within the application to ensure that sensitive data is not misused or stolen. One of the solutions is to use role-based access control (RBAC). Role-based access control (RBAC) is an access control model based on the relationship between users and roles. The core idea of ??this model is to link the user's role to the access control operation, rather than linking the access control operation directly to the user. This approach improves the flexibility of access control,
 Sensitive data leakage and solutions encountered during Go development
Jun 30, 2023 pm 07:55 PM
Sensitive data leakage and solutions encountered during Go development
Jun 30, 2023 pm 07:55 PM
Sensitive data leakage problems and solutions encountered in Go language development Introduction: With the popularization of the Internet and the rapid development of information technology, a large amount of sensitive data is stored and transmitted. The issue of sensitive data leakage has also become a serious challenge. For Go language developers, protecting the security of sensitive data is crucial. This article will discuss sensitive data leakage issues that may be encountered in Go language development and provide solutions. 1. Types of sensitive data leakage issues 1.1 Sensitive data in configuration files during the development process of Go language
 How Nginx implements access control configuration based on request source IP
Nov 08, 2023 am 10:09 AM
How Nginx implements access control configuration based on request source IP
Nov 08, 2023 am 10:09 AM
How Nginx implements access control configuration based on the request source IP requires specific code examples. In network application development, protecting the server from malicious attacks is a very important step. Using Nginx as a reverse proxy server, we can configure IP access control to restrict access to specific IP addresses to improve server security. This article will introduce how to implement access control configuration based on request source IP in Nginx and provide specific code examples. First, we need to edit the Nginx configuration file
 How to verify the domain name of an email address using regular expressions in golang
Jun 24, 2023 am 08:12 AM
How to verify the domain name of an email address using regular expressions in golang
Jun 24, 2023 am 08:12 AM
It is necessary to use regular expressions to verify the domain name of email addresses in golang, because email addresses are very common in practical applications, and the rules for email addresses are also relatively complex. In many cases, we need to verify whether the domain name of the email address entered by the user meets the specifications to ensure the validity and security of the data. This article will introduce how to use regular expressions to verify the domain name of an email address in golang. First, we need to understand the basic rules of email addresses. The email address consists of two parts: "username" and "domain name"





