What is the overall design method of java Dubbo architecture?
Apr 27, 2023 pm 09:52 PM1. Dubbo calling relationship description
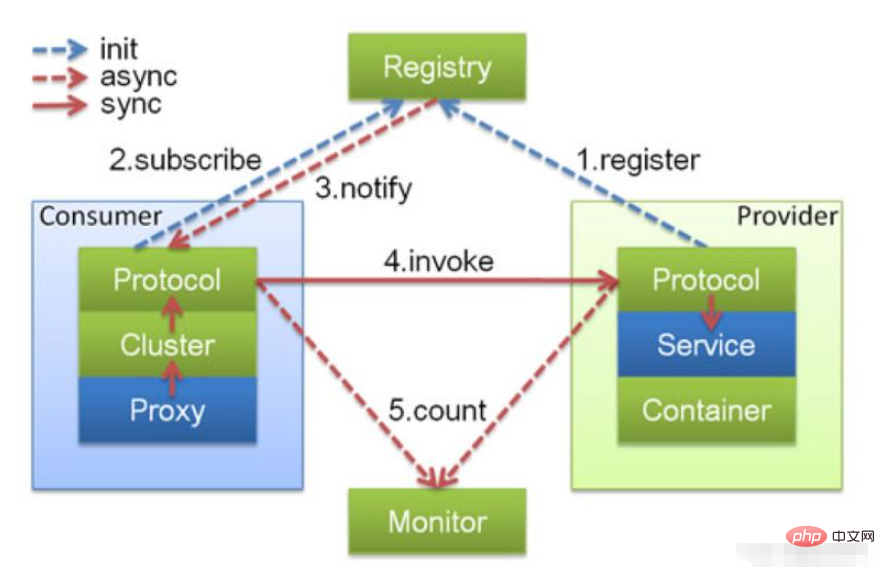
Here It is mainly composed of four parts:
● Provider: the service provider that exposes the serviceProtocol: responsible for the protocol interaction data between the provider and the consumer
Service: the real business service Information can be understood as interfaces and implementations
Container: Dubbo's operating environment
● Consumer: The service consumer that calls the remote service
Protocol: Responsible for the protocol interaction data between the provider and the consumer
Cluster: Perceives the list information on the provider side
Proxy: It can be understood as the provider's service calling proxy, which takes over the interface calling logic in the Consumer
● Register: Registration center, used for service discovery and routing configuration, etc. Work, providers and consumers will be registered here
● Monitor: used for data statistics on providers and consumers, such as call frequency, number of successes and failures, etc.
● When the consumer side starts, it senses the provider information by listening to the provider list, and When the provider changes, the consumer is promptly notified through the registration center
● The consumer initiates a request through the Proxy module;
● The consumer uses the Cluster module to select the real provider to be called;
● Consumer Use the Protocol in the Consumer to send the information to the provider;
● The provider processes consumer information through the Protocol module;
● Finally, the provider's Service handles the processing
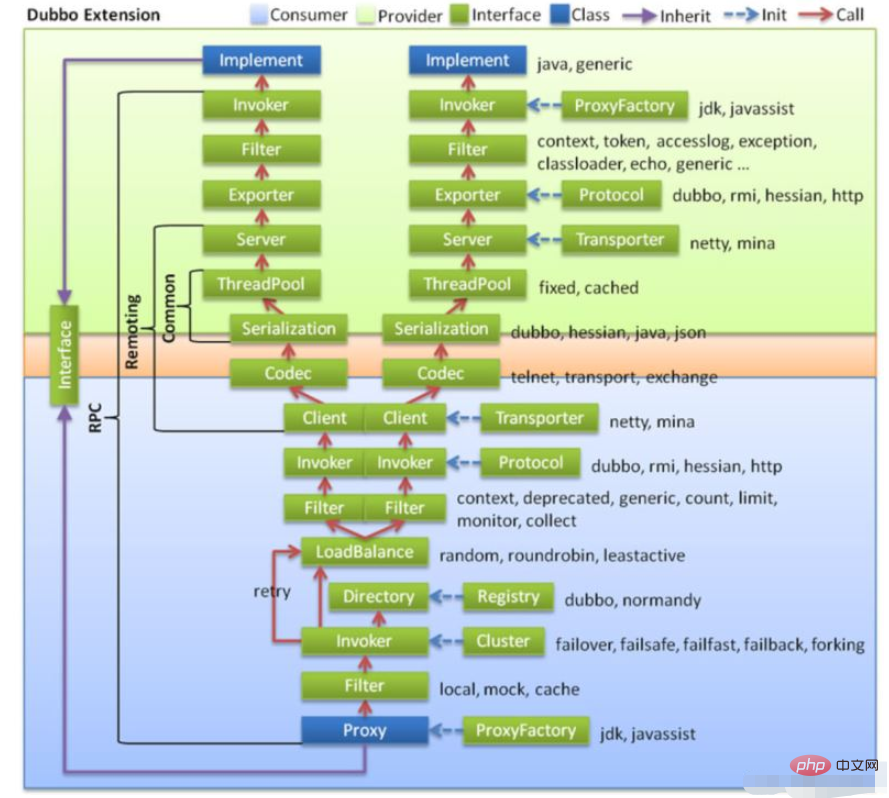
The overall calling process is as follows:
● Consumers call methods through the Interface, unified It is handed over to the Proxy on the consumer side and the proxy object is created through ProxyFactory. The javassist technology of jdk is used here● It is handed over to the Filter module to make unified filtering requests
● Next is the most important Invoker calling logic
○ Read information from the configuration through Directory, and finally obtain all Invokers through the list method
○ Through the Cluster module, select the Invoker list according to the selected specific routing rules
○ Through the LoadBalance module, according to the load balancing policy Select a specific Invoker to handle the request
○ If an error occurs during execution, and the retry mechanism is configured in the Consumer stage, the execution will be retried
● Continue to use the Filter to encapsulate the execution function before and after, and the Invoker selects a specific Invoker Execute the protocol
● The client performs encoding and serialization, and then sends the data
● Reach the Server layer in the Provider to decode and serialize the received data
● Use Exporter to select the executor
● Let the Filter perform a provider-side filtering and reach the Invoker executor
● Call the specific implementation of the interface through the Invoker, and then return the result
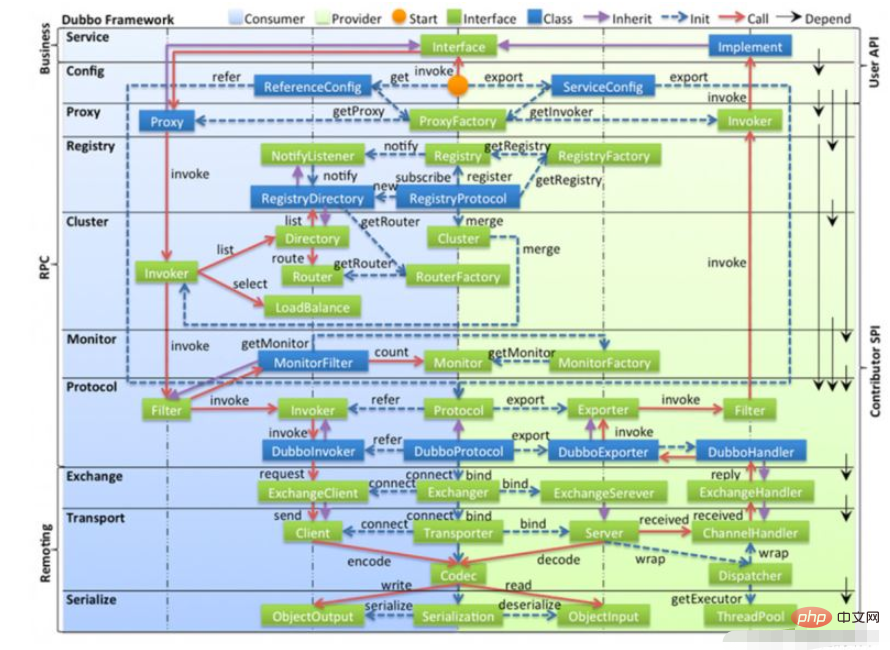
Legend:
● In the figure, the light blue background on the left is the interface used by the service consumer, and the light green background on the right is the interface used by the service provider. The interface located on the central axis is used by both parties.● The figure is divided into ten layers from top to bottom. Each layer has one-way dependencies. The black arrow on the right represents the dependency relationship between layers. Each layer can be stripped off the upper layer and reused. Among them, the Service and Config layers is an API, and all other layers are SPI
● The green blocks in the picture are extension interfaces, and the blue blocks are implementation classes. The picture only shows the implementation classes used to associate each layer
● The blue blocks in the picture are The dotted line is the initialization process, that is, the assembly chain at startup. The solid red line is the method calling process, that is, the runtime call chain. The purple arrow is inheritance. The subclass can be regarded as the same node of the parent class. The text on the line is the call Methods.
The following is a layered introduction
1. Business logic layer
● Service business layer: including business code such as interfaces and implementation classes
2. RPC layer: remote procedure call layer
● config configuration layer, which provides configuration to the outside world. ServiceConfig and ReferenceConfig are the core, which can directly initialize the configuration class or parse the configuration file
● Proxy service agent layer, whether it is a producer or a consumer, the framework will generate a proxy class. The whole process is transparent to the upper layer, and the business layer Remote calls are insensitive
● Register registration center layer, which encapsulates the registration and discovery of service addresses, with the service URL as the center
● Cluster routing layer (cluster fault-tolerant layer), provides routing and load for multiple providers Balanced, and it bridges the registration center with Invoker as the center
● Monitor monitoring layer, RPC call-related information, such as the number of calls, failure situations, call time and other statistical information will be completed in this layer
● Protocol remote The call layer, which encapsulates RPC calls, whether it is service exposure or service reference, is responsible for the entire life cycle of Invoker as the main function entrance in Protocol. All models in Dubbo move closer to Invoker
3. Rmoting layer: Remote data transmission layer
● Exchange information exchange layer, encapsulates the request and response mode, converts the request from synchronous to asynchronous
● Transport network transport layer, unifies the network transmission interface, such as Netty and mina unified into one network Transmission interface
● Serialize data serialization layer, responsible for managing the serialization and deserialization of data transmission in the entire framework
The above is the detailed content of What is the overall design method of java Dubbo architecture?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 VSCode settings.json location
Aug 01, 2025 am 06:12 AM
VSCode settings.json location
Aug 01, 2025 am 06:12 AM
The settings.json file is located in the user-level or workspace-level path and is used to customize VSCode settings. 1. User-level path: Windows is C:\Users\\AppData\Roaming\Code\User\settings.json, macOS is /Users//Library/ApplicationSupport/Code/User/settings.json, Linux is /home//.config/Code/User/settings.json; 2. Workspace-level path: .vscode/settings in the project root directory
 How to handle transactions in Java with JDBC?
Aug 02, 2025 pm 12:29 PM
How to handle transactions in Java with JDBC?
Aug 02, 2025 pm 12:29 PM
To correctly handle JDBC transactions, you must first turn off the automatic commit mode, then perform multiple operations, and finally commit or rollback according to the results; 1. Call conn.setAutoCommit(false) to start the transaction; 2. Execute multiple SQL operations, such as INSERT and UPDATE; 3. Call conn.commit() if all operations are successful, and call conn.rollback() if an exception occurs to ensure data consistency; at the same time, try-with-resources should be used to manage resources, properly handle exceptions and close connections to avoid connection leakage; in addition, it is recommended to use connection pools and set save points to achieve partial rollback, and keep transactions as short as possible to improve performance.
 Mastering Dependency Injection in Java with Spring and Guice
Aug 01, 2025 am 05:53 AM
Mastering Dependency Injection in Java with Spring and Guice
Aug 01, 2025 am 05:53 AM
DependencyInjection(DI)isadesignpatternwhereobjectsreceivedependenciesexternally,promotingloosecouplingandeasiertestingthroughconstructor,setter,orfieldinjection.2.SpringFrameworkusesannotationslike@Component,@Service,and@AutowiredwithJava-basedconfi
 python itertools combinations example
Jul 31, 2025 am 09:53 AM
python itertools combinations example
Jul 31, 2025 am 09:53 AM
itertools.combinations is used to generate all non-repetitive combinations (order irrelevant) that selects a specified number of elements from the iterable object. Its usage includes: 1. Select 2 element combinations from the list, such as ('A','B'), ('A','C'), etc., to avoid repeated order; 2. Take 3 character combinations of strings, such as "abc" and "abd", which are suitable for subsequence generation; 3. Find the combinations where the sum of two numbers is equal to the target value, such as 1 5=6, simplify the double loop logic; the difference between combinations and arrangement lies in whether the order is important, combinations regard AB and BA as the same, while permutations are regarded as different;
 python pytest fixture example
Jul 31, 2025 am 09:35 AM
python pytest fixture example
Jul 31, 2025 am 09:35 AM
fixture is a function used to provide preset environment or data for tests. 1. Use the @pytest.fixture decorator to define fixture; 2. Inject fixture in parameter form in the test function; 3. Execute setup before yield, and then teardown; 4. Control scope through scope parameters, such as function, module, etc.; 5. Place the shared fixture in conftest.py to achieve cross-file sharing, thereby improving the maintainability and reusability of tests.
 Understanding the Java Virtual Machine (JVM) Internals
Aug 01, 2025 am 06:31 AM
Understanding the Java Virtual Machine (JVM) Internals
Aug 01, 2025 am 06:31 AM
TheJVMenablesJava’s"writeonce,runanywhere"capabilitybyexecutingbytecodethroughfourmaincomponents:1.TheClassLoaderSubsystemloads,links,andinitializes.classfilesusingbootstrap,extension,andapplicationclassloaders,ensuringsecureandlazyclassloa
 How to work with Calendar in Java?
Aug 02, 2025 am 02:38 AM
How to work with Calendar in Java?
Aug 02, 2025 am 02:38 AM
Use classes in the java.time package to replace the old Date and Calendar classes; 2. Get the current date and time through LocalDate, LocalDateTime and LocalTime; 3. Create a specific date and time using the of() method; 4. Use the plus/minus method to immutably increase and decrease the time; 5. Use ZonedDateTime and ZoneId to process the time zone; 6. Format and parse date strings through DateTimeFormatter; 7. Use Instant to be compatible with the old date types when necessary; date processing in modern Java should give priority to using java.timeAPI, which provides clear, immutable and linear
 Google Chrome cannot open local files
Aug 01, 2025 am 05:24 AM
Google Chrome cannot open local files
Aug 01, 2025 am 05:24 AM
ChromecanopenlocalfileslikeHTMLandPDFsbyusing"Openfile"ordraggingthemintothebrowser;ensuretheaddressstartswithfile:///;2.SecurityrestrictionsblockAJAX,localStorage,andcross-folderaccessonfile://;usealocalserverlikepython-mhttp.server8000tor






