 Database
Database
 Mysql Tutorial
Mysql Tutorial
 Can the primary key in mysql be empty? Does the primary key constraint allow null values?
Can the primary key in mysql be empty? Does the primary key constraint allow null values?
Can the primary key in mysql be empty? Does the primary key constraint allow null values?
May 28, 2025 pm 06:24 PMThe primary key cannot be empty in MySQL. The primary key ensures the uniqueness and integrity of the data, because the NULL values ??are not considered equal. When selecting a primary key, you need to consider: 1. Uniqueness, ensuring that each row of data is uniquely identified; 2. Immutability, the primary key value should not be modified; 3. Non-empty, the primary key cannot contain NULL values.
In MySQL, whether a primary key can be null is a very interesting and often contributing question. Let me answer this question directly first: the primary key cannot be empty in MySQL.
Why can't the primary key be empty?
A primary key is a column or combination of columns in a table that uniquely identifies each row. It exists to ensure the integrity and uniqueness of the data. If the primary key is allowed to be null, this uniqueness is broken because the NULL value is not considered equal in SQL. Therefore, in MySQL database design, the primary key column is implicitly defined as NOT NULL.
Design and use of primary keys
In actual database design, there are many factors that need to be considered when selecting primary keys:
- Uniqueness : The primary key must be able to uniquely identify each row of data. If you consider using a column as the primary key, the value of this column must be unique throughout the table.
- Immutability : Once the value of the primary key is set, it should not be modified normally. Changing the primary key can cause confusion in the data relationship.
- Non-empty : As mentioned earlier, the primary key cannot contain a NULL value.
Code Example
Let's look at a simple example showing how to create a table in MySQL and set the primary key:
CREATE TABLE users (
user_id INT AUTO_INCREMENT,
username VARCHAR(50) NOT NULL,
email VARCHAR(100) NOT NULL,
PRIMARY KEY (user_id)
); In this example, user_id is set as the primary key, and a unique value is automatically generated using AUTO_INCREMENT to ensure that each row has a unique identifier.
Experience sharing in practice
In my career, I have encountered problems with some developers trying to use columns that can be null as primary keys, resulting in confusion in data and difficult to track. Once, a team used the user's mailbox as the primary key. The problem was that the user could modify the mailbox, which led to the emergence of data consistency problems. Finally, we decided to use an automatically generated ID as the primary key and use the mailbox as the unique index, which not only ensures the uniqueness of the data, but also allows users to modify the mailbox.
Pros and cons and pitfalls
- Advantages : Using primary keys can improve query efficiency, especially when performing JOIN operations. Primary keys can also help optimize the physical storage of data, making data retrieval faster.
- Disadvantages : If the primary key is selected incorrectly (such as using too long strings), performance may be affected. In addition, if the primary key changes frequently, it will increase the complexity of database maintenance.
- Pit point : When using composite primary keys, make sure that all columns cannot be empty, otherwise the primary key constraint will fail. In addition, when using the auto-increment primary key, pay attention to the auto-increment management to avoid the problem of auto-increment discontinuous due to restarting the database or other operations.
in conclusion
In short, the primary key in MySQL cannot be empty, which is to ensure the uniqueness and integrity of the data. When designing a database, choosing the right primary key is a very critical step, which not only affects the structure of the data, but also affects the subsequent query performance and the complexity of data maintenance. Through reasonable design and accumulation of practical experience, we can better utilize primary keys to build an efficient and robust database system.
The above is the detailed content of Can the primary key in mysql be empty? Does the primary key constraint allow null values?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Why is Bitcoin with a ceiling? Why is the maximum number of Bitcoins 21 million
Jul 30, 2025 pm 10:30 PM
Why is Bitcoin with a ceiling? Why is the maximum number of Bitcoins 21 million
Jul 30, 2025 pm 10:30 PM
The total amount of Bitcoin is 21 million, which is an unchangeable rule determined by algorithm design. 1. Through the proof of work mechanism and the issuance rule of half of every 210,000 blocks, the issuance of new coins decreased exponentially, and the additional issuance was finally stopped around 2140. 2. The total amount of 21 million is derived from summing the equal-scale sequence. The initial reward is 50 bitcoins. After each halving, the sum of the sum converges to 21 million. It is solidified by the code and cannot be tampered with. 3. Since its birth in 2009, all four halving events have significantly driven prices, verified the effectiveness of the scarcity mechanism and formed a global consensus. 4. Fixed total gives Bitcoin anti-inflation and digital yellow metallicity, with its market value exceeding US$2.1 trillion in 2025, becoming the fifth largest capital in the world
 Ethereum (ETH) NFT sold nearly $160 million in seven days, and lenders launched unsecured crypto loans with World ID
Jul 30, 2025 pm 10:06 PM
Ethereum (ETH) NFT sold nearly $160 million in seven days, and lenders launched unsecured crypto loans with World ID
Jul 30, 2025 pm 10:06 PM
Table of Contents Crypto Market Panoramic Nugget Popular Token VINEVine (114.79%, Circular Market Value of US$144 million) ZORAZora (16.46%, Circular Market Value of US$290 million) NAVXNAVIProtocol (10.36%, Circular Market Value of US$35.7624 million) Alpha interprets the NFT sales on Ethereum chain in the past seven days, and CryptoPunks ranked first in the decentralized prover network Succinct launched the Succinct Foundation, which may be the token TGE
 What is Binance Treehouse (TREE Coin)? Overview of the upcoming Treehouse project, analysis of token economy and future development
Jul 30, 2025 pm 10:03 PM
What is Binance Treehouse (TREE Coin)? Overview of the upcoming Treehouse project, analysis of token economy and future development
Jul 30, 2025 pm 10:03 PM
What is Treehouse(TREE)? How does Treehouse (TREE) work? Treehouse Products tETHDOR - Decentralized Quotation Rate GoNuts Points System Treehouse Highlights TREE Tokens and Token Economics Overview of the Third Quarter of 2025 Roadmap Development Team, Investors and Partners Treehouse Founding Team Investment Fund Partner Summary As DeFi continues to expand, the demand for fixed income products is growing, and its role is similar to the role of bonds in traditional financial markets. However, building on blockchain
 What is Ethereum? What are the ways to obtain Ethereum ETH?
Jul 31, 2025 pm 11:00 PM
What is Ethereum? What are the ways to obtain Ethereum ETH?
Jul 31, 2025 pm 11:00 PM
Ethereum is a decentralized application platform based on smart contracts, and its native token ETH can be obtained in a variety of ways. 1. Register an account through centralized platforms such as Binance and Ouyiok, complete KYC certification and purchase ETH with stablecoins; 2. Connect to digital storage through decentralized platforms, and directly exchange ETH with stablecoins or other tokens; 3. Participate in network pledge, and you can choose independent pledge (requires 32 ETH), liquid pledge services or one-click pledge on the centralized platform to obtain rewards; 4. Earn ETH by providing services to Web3 projects, completing tasks or obtaining airdrops. It is recommended that beginners start from mainstream centralized platforms, gradually transition to decentralized methods, and always attach importance to asset security and independent research, to
 What is Huobi HTX red envelope? How to send and receive red envelopes? Huobi divides 1000U activities
Jul 30, 2025 pm 09:45 PM
What is Huobi HTX red envelope? How to send and receive red envelopes? Huobi divides 1000U activities
Jul 30, 2025 pm 09:45 PM
Table of Contents 1. What is Huobi HTX red envelope? 2. How to create and send red envelopes? 3. How to receive red envelopes? 1. Receive password red envelopes 2. Scan the QR code to receive red envelopes 3. Click on the red envelope link to receive red envelopes 4. Check the red envelopes and share more instructions: 1. What is Huobi HTX red envelope? Huobi HTX red envelopes support users to send cryptocurrencies to friends in the form of red envelopes. You can create cryptocurrency red envelopes with random or fixed amounts, and send them to friends by sending red envelope passwords, sharing links or posters. Your friends can receive it for free in Huobi HTXAPP or click on the link. Huobi HTX red envelopes also support unregistered users to receive them, and
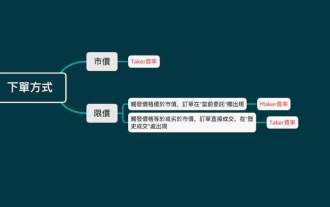 What are Maker and Taker? How to calculate the handling fee? A list of handling fees on popular exchanges
Jul 30, 2025 pm 09:33 PM
What are Maker and Taker? How to calculate the handling fee? A list of handling fees on popular exchanges
Jul 30, 2025 pm 09:33 PM
What are directory Maker and pending orders? How to calculate MakerFee? MakerFee calculation formula. Is it necessary to use limit orders? Taker and eat orders? How to calculate TakerFee How to determine whether you are Maker or Taker lazy package – Maker/taker fee spot maker/taker fee lazy package contract maker/taker fee lazy package How to reduce Maker/taker transaction fees for various virtual currency exchanges
 Why do you say you choose altcoins in a bull market and buy BTC in a bear market
Jul 30, 2025 pm 10:27 PM
Why do you say you choose altcoins in a bull market and buy BTC in a bear market
Jul 30, 2025 pm 10:27 PM
The strategy of choosing altcoins in a bull market, and buying BTC in a bear market is established because it is based on the cyclical laws of market sentiment and asset attributes: 1. In the bull market, altcoins are prone to high returns due to their small market value, narrative-driven and liquidity premium; 2. In the bear market, Bitcoin has become the first choice for risk aversion due to scarcity, liquidity and institutional consensus; 3. Historical data shows that the increase in the bull market altcoins in 2017 far exceeded that of Bitcoin, and the decline in the bear market in 2018 was also greater. In 2024, funds in the volatile market will be further concentrated in BTC; 4. Risk control needs to be vigilant about manipulating traps, buying at the bottom and position management. It is recommended that the position of altcoins in a bull market shall not exceed 30%, and the position holdings of BTC in a bear market can be increased to 70%; 5. In the future, due to institutionalization, technological innovation and macroeconomic environment, the strategy needs to be dynamically adjusted to adapt to market evolution.
 Solana and the founders of Base Coin start a debate: the content on Zora has 'basic value'
Jul 30, 2025 pm 09:24 PM
Solana and the founders of Base Coin start a debate: the content on Zora has 'basic value'
Jul 30, 2025 pm 09:24 PM
A verbal battle about the value of "creator tokens" swept across the crypto social circle. Base and Solana's two major public chain helmsmans had a rare head-on confrontation, and a fierce debate around ZORA and Pump.fun instantly ignited the discussion craze on CryptoTwitter. Where did this gunpowder-filled confrontation come from? Let's find out. Controversy broke out: The fuse of Sterling Crispin's attack on Zora was DelComplex researcher Sterling Crispin publicly bombarded Zora on social platforms. Zora is a social protocol on the Base chain, focusing on tokenizing user homepage and content





