This tutorial demonstrates face detection and recognition using Python, leveraging the MTCNN and VGGFace2 models. We'll learn to identify faces in images, extract them, and compare them to determine if they belong to the same individual.
This process involves several key steps:
-
Face Detection with MTCNN: We utilize the pre-trained MTCNN model in Keras to locate and extract faces from images. This model efficiently identifies facial features and bounding boxes.
-
Face Recognition with VGGFace2: Once faces are extracted, the VGGFace2 model compares their features to assess similarity. This model, developed by Oxford's Visual Geometry Group, excels at recognizing individuals.
-
Image Preprocessing and Handling: The tutorial covers essential image handling using
matplotlibfor reading and manipulating images andPILfor resizing. -
Model Comparison and Thresholds: We'll learn how to compare faces using cosine similarity, a metric well-suited for comparing feature vectors. The importance of setting appropriate thresholds for accurate face recognition will be highlighted.
Prerequisites:
Before beginning, install the necessary Python libraries:
pip3 install matplotlib keras mtcnn keras_vggface
Step-by-Step Guide:
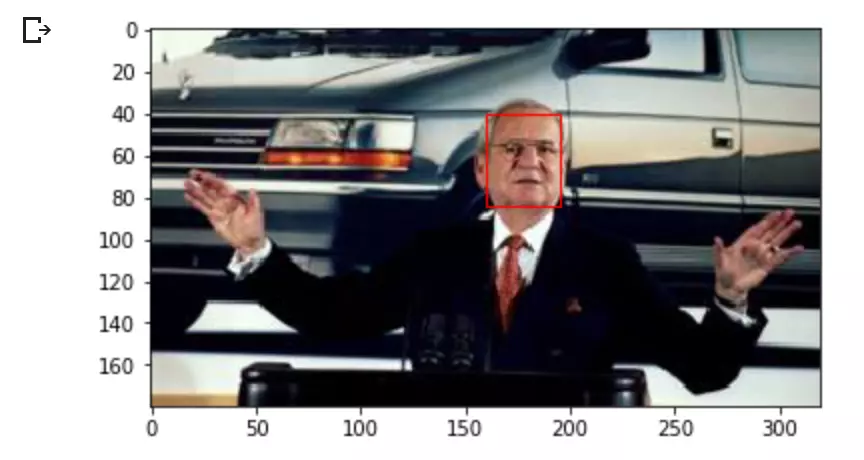
The tutorial demonstrates the process using images of Lee Iacocca and Chelsea Football Club players. It covers:
-
Retrieving External Images: A
store_imagefunction downloads images from URLs and saves them locally. -
Face Detection: The
MTCNNmodel is used to detect faces, providing bounding boxes and confidence scores. - Highlighting Faces: A visualization function draws rectangles around detected faces for verification.
- Face Extraction: Faces are extracted from images and resized to 224x224 pixels for compatibility with VGGFace2.
-
Face Comparison: The
VGGFace2model generates feature vectors for each face, and cosine similarity is used to compare them. A threshold determines whether faces are considered a match.

Key Considerations:
- Threshold Selection: The choice of similarity threshold significantly impacts accuracy. Experimentation and careful consideration of factors like lighting and pose are crucial.
- Model Limitations: The accuracy of face recognition can be affected by variations in pose, expression, and image quality.
Conclusion:
This tutorial provides a practical introduction to face detection and recognition using readily available pre-trained models. While building and training your own model requires significant resources, this approach offers a quick and effective solution for many applications. Remember to adjust thresholds and consider model limitations for optimal results.
Frequently Asked Questions (FAQs):
The FAQs section addresses common questions about CNNs, VGGFace2, model accuracy improvement, Keras' role, comparisons with ML Kit and FaceNet, real-world applications, and challenges in face detection and recognition. These FAQs provide a comprehensive understanding of the underlying concepts and techniques.
The above is the detailed content of Face Detection and Recognition with Keras. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Advanced AI models generate up to 50 times more CO₂ emissions than more common LLMs when answering the same questions
Jul 06, 2025 am 12:37 AM
Advanced AI models generate up to 50 times more CO₂ emissions than more common LLMs when answering the same questions
Jul 06, 2025 am 12:37 AM
The more precisely we attempt to make AI models function, the greater their carbon emissions become — with certain prompts generating up to 50 times more carbon dioxide than others, according to a recent study.Reasoning models like Anthropic's Claude
 AI 'hallucinates' constantly, but there's a solution
Jul 07, 2025 am 01:26 AM
AI 'hallucinates' constantly, but there's a solution
Jul 07, 2025 am 01:26 AM
The major concern with big tech experimenting with artificial intelligence (AI) isn't that it might dominate humanity. The real issue lies in the persistent inaccuracies of large language models (LLMs) such as Open AI's ChatGPT, Google's Gemini, and
 Why is AI halllucinating more frequently, and how can we stop it?
Jul 08, 2025 am 01:44 AM
Why is AI halllucinating more frequently, and how can we stop it?
Jul 08, 2025 am 01:44 AM
The more advanced artificial intelligence (AI) becomes, the more it tends to "hallucinate" and provide false or inaccurate information.According to research by OpenAI, its most recent and powerful reasoning models—o3 and o4-mini—exhibited h
 Cutting-edge AI models from OpenAI and DeepSeek undergo 'complete collapse' when problems get too difficult, study reveals
Jul 07, 2025 am 01:02 AM
Cutting-edge AI models from OpenAI and DeepSeek undergo 'complete collapse' when problems get too difficult, study reveals
Jul 07, 2025 am 01:02 AM
Artificial intelligence (AI) reasoning models aren't quite as capable as they appear. In reality, their performance breaks down completely when tasks become too complex, according to researchers at Apple.Reasoning models like Anthropic's Claude, Open
 Arrests made in hunt for hackers behind cyber attacks on M&S and Co-op
Jul 11, 2025 pm 01:36 PM
Arrests made in hunt for hackers behind cyber attacks on M&S and Co-op
Jul 11, 2025 pm 01:36 PM
The UK’s National Crime Agency (NCA) has arrested four individuals suspected of involvement in the cyber attacks targeting Marks and Spencer (M&S), Co-op, and Harrods.According to a statement, the suspects include two 19-year-old men, a 17-year-o
 Post-quantum cryptography is now top of mind for cybersecurity leaders
Jul 11, 2025 pm 01:38 PM
Post-quantum cryptography is now top of mind for cybersecurity leaders
Jul 11, 2025 pm 01:38 PM
Post-quantum cryptography has become a top priority for cybersecurity leaders, yet recent research indicates that some organizations are not treating the threat with the seriousness it demands.Quantum computers will eventually be capable of solving t
 Ransomware attacks carry huge financial impacts – but CISO worries still aren’t stopping firms from paying out
Jul 12, 2025 am 12:59 AM
Ransomware attacks carry huge financial impacts – but CISO worries still aren’t stopping firms from paying out
Jul 12, 2025 am 12:59 AM
Ransomware attacks bring with them an average recovery cost of $4.5 million, according to a recent survey, which also found that a significant number of businesses have been affected by the malware in the past year.Data collected by Absolute Security
 Red Hat is giving developers free access to RHEL – here’s what you need to know
Jul 13, 2025 am 12:49 AM
Red Hat is giving developers free access to RHEL – here’s what you need to know
Jul 13, 2025 am 12:49 AM
Red Hat has introduced a new self-service platform designed to provide easier access to its developer program.The Red Hat Enterprise Linux for Business Developers initiative is intended to assist development teams in building, testing, and deploying






