Found a total of 10000 related content

Python Cryptography Library Usage
Article Introduction:The Python encryption library is used as follows: 1. Symmetric encryption is recommended to use the Fernet module in the cryptography library. The key is generated by generate_key() and the data is encrypted and decrypted with encrypt()/decrypt(); 2. The hashlib library can be used to calculate hashlib, and the SHA256 algorithm is preferred and the hash value is obtained through hexdigest(). Pay attention to avoiding MD5 and SHA1; 3. Asymmetric encryption can use the RSA function of cryptography to generate key pairs through generate_private_key(), and use public key encryption and private key decryption. Note that filling schemes such as OAEP must be used and only suitable
2025-07-17
comment 0
522

How does Laravel's service container use reflection for auto-wiring?
Article Introduction:Laravel's container uses the PHP reflection API to automatically parse class dependencies to achieve automatic assembly; 1. When requesting to parse a class, if the constructor parameter has a type prompt and can be parsed, it can be instantiated without explicit binding; 2. The container obtains constructor parameters through ReflectionClass, uses ReflectionParameter to read the type prompt and recursively parse each dependency; 3. Reliability is recursively parsed according to the graph, such as the OrderController relies on the OrderService, which relies on the OrderRepository, and finally builds layer by layer from the bottom layer; 4. If the parameter has no type prompt, is a basic type or has no binding to the interface, an exception is thrown unless provided
2025-07-25
comment 0
825

PHP Master | Logging with PSR-3 to Improve Reusability
Article Introduction:Core points
PSR-3, a common log object interface, allows developers to write reusable code without relying on any specific log implementation, thereby improving compatibility between different log libraries in PHP.
The PSR-3 interface provides eight methods to handle messages of different severity levels, and a common log() method that can receive any severity levels. Its design is to solve the problem of log implementation incompatibility.
Although PSR-3 has many benefits, some log libraries do not support it natively. However, developers can create PSR-3 compliant adapters by leveraging the adapter pattern and extending the AbstractLogger class provided in the Psr/Log library.
Many major PHP projects
2025-02-24
comment 0
1267

What are Weak Maps in PHP?
Article Introduction:PHP does not have a built-in WeakMap type, but similar functions can be implemented through the WeakMap class provided by the WeakrefPECL extension. The key feature of WeakMap is that its keys are stored in a weak reference manner, avoiding preventing garbage collection and thus preventing memory leaks. When using it, you must first install and enable the Weakref extension. After creating a WeakMap instance, the object is stored as a key, and it will be automatically cleaned when there are no other references to the object. Applicable scenarios include: 1. Cache object-related data; 2. Add metadata to the object; 3. Avoid memory leaks in the event system. Notes include: 1. WeakMap is not a PHP core function; 2. The key must be an object; 3. The entry clearing time is uncontrollable. If the deployment environment allows,
2025-06-27
comment 0
365


Dave The Diver: How To Catch Spider Crabs
Article Introduction:In Dave The Diver, there are some creatures that are not easy to catch. Or, catch alive that is. The spider crab is one of those very species, making it seem like the only way to bring these crustaceans back up to land is to viciously crack them up w
2025-01-10
comment 0
856

Prepare for Interview Like a Pro with Interview Questions CLI
Article Introduction:Prepare for Interview Like a Pro with Interview Questions CLI
What is the Interview Questions CLI?
The Interview Questions CLI is a command-line tool designed for JavaScript learners and developers who want to enhance their interview
2025-01-10
comment 0
1487

Soft Deletes in Databases: To Use or Not to Use?
Article Introduction:Soft Deletes: A Question of DesignThe topic of soft deletes, a mechanism that "flags" records as deleted instead of physically removing them, has...
2025-01-10
comment 0
1083

Terraria: How To Make A Loom
Article Introduction:There are a lot of crafting stations that you can make in Terraria. This ranges from simple anvils to unique stations meant for one specific type of resource. Early into the game, you'll be able to make your own Loom, which is primarily used to make
2025-01-10
comment 0
1365
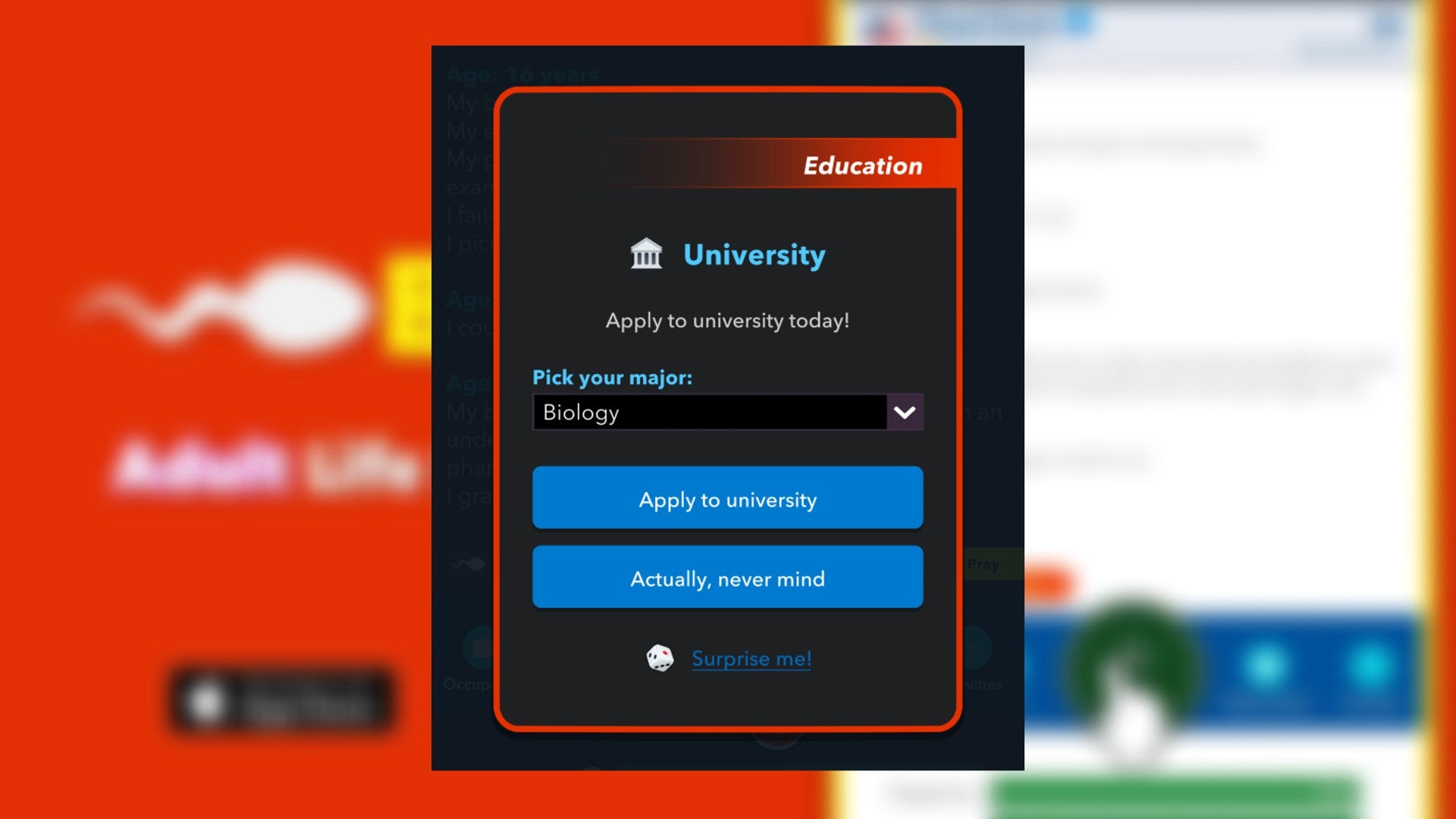
How to become a Mortician in Bitlife
Article Introduction:There are an abundance of job roles to try in Bitlife, and while the best jobs are those that land you with lots of fame and money — such as becoming a Model or an Astronaut — there are plenty other, simpler jobs to get you by. There’s
2025-01-10
comment 0
610



















