Analysis of the functions and principles of JVM virtual machine
Feb 22, 2024 pm 01:54 PM
Analysis of the functions and principles of the JVM virtual machine
Introduction:
JVM (Java Virtual Machine) The virtual machine is one of the core components of the Java programming language. It is one of Java's biggest selling points. The role of the JVM is to compile Java source code into bytecodes and be responsible for executing these bytecodes. This article will introduce the role of JVM and how it works, and provide some code examples to help readers understand better.
Function:
The main function of JVM is to solve the portability problem of Java programs on different platforms. It compiles Java source code into intermediate bytecode, which is then interpreted and executed by the JVM on the target platform. This mechanism enables Java programs to run on any platform that supports JVM without any modification to the source code.
JVM principle analysis:
The working principle of JVM can be divided into three stages: loading, interpretation and execution.
- Loading:
During the loading phase, the JVM is responsible for loading Java bytecode files from the classpath. The class loader finds the corresponding bytecode file based on the fully qualified name of the class, then reads the contents of the bytecode file and converts it into a runtime data structure in memory. The loading phase also includes verifying the structure of the bytecode file to ensure that it conforms to the Java Virtual Machine specification. - Explanation:
In the interpretation phase, the JVM interprets the bytecode instructions line by line and translates them into underlying machine instructions. JVM realizes the interpretation and execution of bytecode through the interpreter, executes the bytecode instructions one by one, and converts them into specific operations. The interpretation phase also includes the division of runtime data areas, the creation of stack frames and the processing of method calls. - Execution:
In the execution phase, the JVM operates the data in the runtime data area according to the bytecode instructions. JVM provides a variety of runtime data areas, such as heap, stack, method area, etc., for storing data during program execution. According to the opcode of the bytecode instruction, the JVM performs corresponding operations, such as loading, storing, and computing variables. The execution phase also involves exception handling, garbage collection and other mechanisms.
Code Example:
The following is a simple Java program example to demonstrate how the JVM works:
public class HelloWorld {
public static void main(String[] args) {
System.out.println("Hello, World!");
}
}After the Java source code is compiled into bytecode, This bytecode can be executed using the JVM. The JVM will load, interpret and execute the bytecode, and output "Hello, World!".
Conclusion:
JVM is the basis for running Java programs. It is responsible for compiling Java source code into bytecodes and executing these bytecodes. The working principle of JVM includes three stages: loading, interpretation and execution. By using the JVM, Java programs can achieve cross-platform portability without any modifications to the source code.
In short, the functions and principles of the JVM virtual machine can be simply summarized as loading, interpretation and execution. Through the JVM, Java programs can achieve cross-platform portability, providing developers with higher flexibility and scalability. At the same time, you can use sample code to understand the working principle of the JVM more intuitively.
The above is the detailed content of Analysis of the functions and principles of JVM virtual machine. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Analysis of the function and principle of nohup
Mar 25, 2024 pm 03:24 PM
Analysis of the function and principle of nohup
Mar 25, 2024 pm 03:24 PM
Analysis of the role and principle of nohup In Unix and Unix-like operating systems, nohup is a commonly used command that is used to run commands in the background. Even if the user exits the current session or closes the terminal window, the command can still continue to be executed. In this article, we will analyze the function and principle of the nohup command in detail. 1. The role of nohup: Running commands in the background: Through the nohup command, we can let long-running commands continue to execute in the background without being affected by the user exiting the terminal session. This needs to be run
 Three simple and effective ways to transfer files from VMware virtual machines
Mar 15, 2024 am 09:22 AM
Three simple and effective ways to transfer files from VMware virtual machines
Mar 15, 2024 am 09:22 AM
When we use Vmware virtual machines, we may encounter situations where we don’t know how to copy files into the virtual machine. In fact, the method is very simple. Below, the editor has brought three methods to users. Interested users can take a closer look. Let’s take a look. Three simple and effective methods to transfer files to VMware virtual machines Method 1: VMWareTools To install VMWaretools, click on the virtual machine above - Install VMwaretools. After the installation is successful, you can copy and paste the file to the virtual machine. After the installation is successful, the following content will be displayed: After the installation is successful, you can drag the file directly, or copy and paste it through ctrl+Cctrl+V. If found unable
 In-depth understanding of the batch Insert implementation principle in MyBatis
Feb 21, 2024 pm 04:42 PM
In-depth understanding of the batch Insert implementation principle in MyBatis
Feb 21, 2024 pm 04:42 PM
MyBatis is a popular Java persistence layer framework that is widely used in various Java projects. Among them, batch insertion is a common operation that can effectively improve the performance of database operations. This article will deeply explore the implementation principle of batch Insert in MyBatis, and analyze it in detail with specific code examples. Batch Insert in MyBatis In MyBatis, batch Insert operations are usually implemented using dynamic SQL. By constructing a line S containing multiple inserted values
 What are the virtualization software?
Feb 23, 2024 pm 02:42 PM
What are the virtualization software?
Feb 23, 2024 pm 02:42 PM
What are the virtualization software? With the continuous development of technology, virtualization technology has become an important concept in the field of modern computer science. The goal of virtualization is to logically divide physical resources such as CPU, memory and storage to form multiple virtual environments so that multiple operating systems and applications can run on the same physical computer at the same time. As a key tool to achieve this goal, virtualization software has received increasing attention and application. This article will introduce some common virtualization software. VMwarevSphere: VMw
 Detailed explanation of the principle of MyBatis paging plug-in
Feb 22, 2024 pm 03:42 PM
Detailed explanation of the principle of MyBatis paging plug-in
Feb 22, 2024 pm 03:42 PM
MyBatis is an excellent persistence layer framework. It supports database operations based on XML and annotations. It is simple and easy to use. It also provides a rich plug-in mechanism. Among them, the paging plug-in is one of the more frequently used plug-ins. This article will delve into the principles of the MyBatis paging plug-in and illustrate it with specific code examples. 1. Paging plug-in principle MyBatis itself does not provide native paging function, but you can use plug-ins to implement paging queries. The principle of paging plug-in is mainly to intercept MyBatis
 An in-depth analysis of the functions and working principles of the Linux chage command
Feb 24, 2024 pm 03:48 PM
An in-depth analysis of the functions and working principles of the Linux chage command
Feb 24, 2024 pm 03:48 PM
The chage command in the Linux system is a command used to modify the password expiration date of a user account. It can also be used to modify the longest and shortest usable date of the account. This command plays a very important role in managing user account security. It can effectively control the usage period of user passwords and enhance system security. How to use the chage command: The basic syntax of the chage command is: chage [option] user name. For example, to modify the password expiration date of user "testuser", you can use the following command
 An in-depth discussion of the functions and principles of Linux RPM tools
Feb 23, 2024 pm 03:00 PM
An in-depth discussion of the functions and principles of Linux RPM tools
Feb 23, 2024 pm 03:00 PM
The RPM (RedHatPackageManager) tool in Linux systems is a powerful tool for installing, upgrading, uninstalling and managing system software packages. It is a commonly used software package management tool in RedHatLinux systems and is also used by many other Linux distributions. The role of the RPM tool is very important. It allows system administrators and users to easily manage software packages on the system. Through RPM, users can easily install new software packages and upgrade existing software
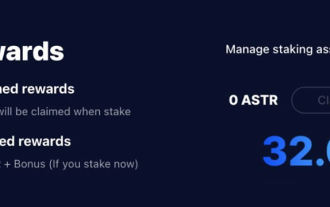 Astar staking principle, income dismantling, airdrop projects and strategies & operation nanny-level strategy
Jun 25, 2024 pm 07:09 PM
Astar staking principle, income dismantling, airdrop projects and strategies & operation nanny-level strategy
Jun 25, 2024 pm 07:09 PM
Table of Contents Astar Dapp Staking Principle Staking Revenue Dismantling of Potential Airdrop Projects: AlgemNeurolancheHealthreeAstar Degens DAOVeryLongSwap Staking Strategy & Operation "AstarDapp Staking" has been upgraded to the V3 version at the beginning of this year, and many adjustments have been made to the staking revenue rules. At present, the first staking cycle has ended, and the "voting" sub-cycle of the second staking cycle has just begun. To obtain the "extra reward" benefits, you need to grasp this critical stage (expected to last until June 26, with less than 5 days remaining). I will break down the Astar staking income in detail,






