 Technology peripherals
Technology peripherals
 It Industry
It Industry
 Alipay launched the 'Chinese Character Picking-Rare Characters' mini program to collect and supplement the rare character library
Alipay launched the 'Chinese Character Picking-Rare Characters' mini program to collect and supplement the rare character library
Alipay launched the 'Chinese Character Picking-Rare Characters' mini program to collect and supplement the rare character library
Oct 31, 2023 pm 09:25 PMNews from this site on October 31st. On May 27th this year, Ant Group announced the launch of the "Chinese Character Picking Project". Recently, new progress has been made: Alipay launched the "Chinese Character Picking-Uncommon Characters" applet for Collect rare characters from the society, replenish the rare character library, and provide different input experiences for rare characters to help improve the rare character input method in Alipay.
Currently, users can enter the "Uncommon Characters" applet by searching for keywords such as "Chinese character pick-up" and "rare characters". In the mini program, users can submit pictures of rare characters that have not been recognized and entered by the system. After confirmation, Alipay engineers will make additional entries into the font library .
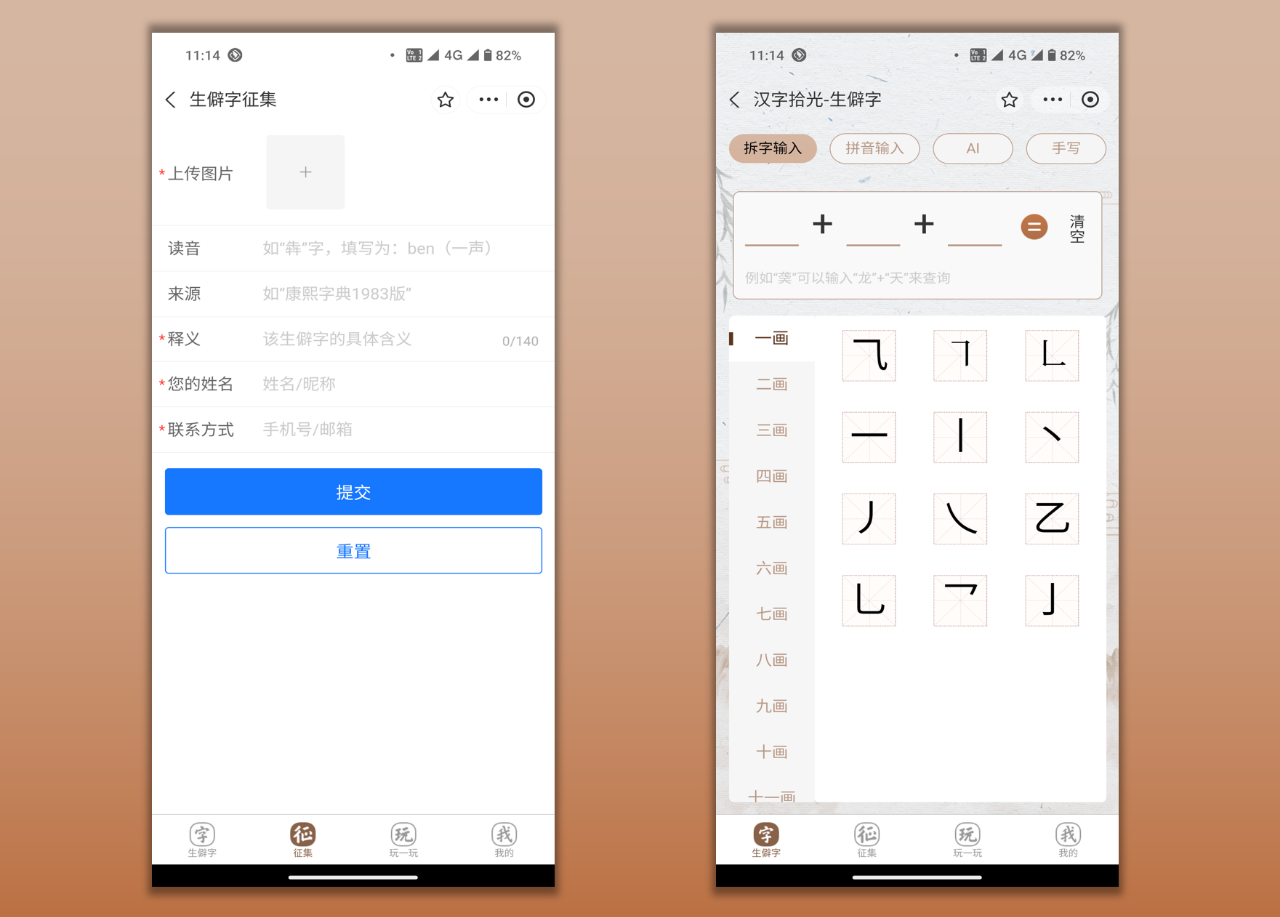
This site noticed that users can also experience the latest split word input method in the mini program. This input method is for Design of rare characters with unclear pronunciation. After the user disassembles the glyphs, the system will recommend possible corresponding rare characters . In the future, this input method will be supplemented by Alipay’s keyboard with uncommon characters to further improve the user experience.

After the solution related to rare characters was launched, nearly 7,000 users whose names contain rare characters have successfully passed Alipay authentication , so that you can smoothly enjoy online services such as government affairs and facial recognition payment on Alipay.
Advertising statement: The external jump links (including but not limited to hyperlinks, QR codes, passwords, etc.) contained in the article are used to convey more information and save selection time. The results are for reference only. All articles on the site contain this statement.
The above is the detailed content of Alipay launched the 'Chinese Character Picking-Rare Characters' mini program to collect and supplement the rare character library. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to trade stablecoins_A full flow diagram for beginners buying and selling
Jul 18, 2025 am 06:00 AM
How to trade stablecoins_A full flow diagram for beginners buying and selling
Jul 18, 2025 am 06:00 AM
The stablecoin trading process includes the steps of registering an exchange, completing certification, buying or selling. First, choose a trusted exchange such as Binance, OKX, etc., and then complete KYC identity authentication, and then buy stablecoins through fiat currency recharge or OTC transactions. You can also transfer the stablecoins to the fund account and sell them through P2P transactions and withdraw them to the bank card or Alipay. When operating, you need to pay attention to choosing a regulated platform, confirm transaction security and handling fees.
 How to download the official Bitcoin app? Bitcoin App Use Guide
Jul 22, 2025 pm 11:54 PM
How to download the official Bitcoin app? Bitcoin App Use Guide
Jul 22, 2025 pm 11:54 PM
Bitcoin does not have an official app, and users mainly trade and manage them through third-party exchanges or account apps. 1. Binance has comprehensive functions and is suitable for all kinds of traders; 2. OKX provides integrated trading and Web3 accounts; 3. Huobi (HTX) is stable and reliable in the Asian market; 4. Gate.io is known for its rich currency; 5. KuCoin has diverse currencies and active communities; 6. Bybit is known for its derivatives trading. When downloading, you should visit the official website, scan the QR code, complete the installation according to the system, and set up security measures such as two-factor verification to ensure the security of the account.
 Answers to Ant New Village on July 17, 2025
Jul 17, 2025 am 06:10 AM
Answers to Ant New Village on July 17, 2025
Jul 17, 2025 am 06:10 AM
Maybe there are many children's shoes who want to know the answers to Ant New Village on July 17, 2025. Let's bring you answers in this regard. Come and have a look.
 Ant New Village Small Classroom Today's Answer July 17th Is the cotton paper used in the ancient books of intangible cultural heritage made of cotton?
Jul 17, 2025 am 06:10 AM
Ant New Village Small Classroom Today's Answer July 17th Is the cotton paper used in the ancient books of intangible cultural heritage made of cotton?
Jul 17, 2025 am 06:10 AM
Maybe there are many children's shoes that don't know the answers of Ant New Village Classroom today July 17th. Is the cotton paper used in the ancient books of intangible cultural heritage made of cotton? Let the editor answer this question below. Let's take a look with me!
 Where is the most convenient transaction for USDT? Full guide to buying and selling USDT (with handling fees and transaction skills instructions)
Jul 22, 2025 pm 07:45 PM
Where is the most convenient transaction for USDT? Full guide to buying and selling USDT (with handling fees and transaction skills instructions)
Jul 22, 2025 pm 07:45 PM
Selecting a platform requires consideration of security, fees, liquidity, experience and support. Priority is given to platforms with good reputation, low fees and strong liquidity, such as Binance, OKEx, etc.; 2. When purchasing USDT, you can go through three ways: C2C (no handling fee but with price difference), credit card (fast but expensive), and currency trading (low cost suitable for currency holders); 3. Selling USDT can take three ways: C2C (direct exchange for fiat currency, pay attention to checking buyer information), fiat currency withdrawal (KYC required), and exchange for other currencies; 4. Transaction fees include order/eating fee (cheap order), withdrawal fee (TRC-20 chain is the most cost-effective), and C2C premiums need to be paid attention to; 5. Trading skills are to first test small amounts, choose the right chain (such as TRC-20), set 2FA to ensure safety, complete KYC increase limit,
 How to build a content payment platform through PHP How to implement PHP paid reading system
Jul 25, 2025 pm 06:30 PM
How to build a content payment platform through PHP How to implement PHP paid reading system
Jul 25, 2025 pm 06:30 PM
To build a PHP content payment platform, it is necessary to build a user management, content management, payment and permission control system. First, establish a user authentication system and use JWT to achieve lightweight authentication; second, design the backend management interface and database fields to manage paid content; third, integrate Alipay or WeChat payment and ensure process security; fourth, control user access rights through session or cookies. Choosing the Laravel framework can improve development efficiency, use watermarks and user management to prevent content theft, optimize performance requires coordinated improvement of code, database, cache and server configuration, and clear policies must be formulated and malicious behaviors must be prevented.
 Ant New Village today's answer 7.17
Jul 17, 2025 am 06:10 AM
Ant New Village today's answer 7.17
Jul 17, 2025 am 06:10 AM
I believe some children's shoes want to know about Ant New Village's answer today. The editor below will bring you the answer. Let's take a look with me!
 Did you know? The evacuation doors for safe exits in public places should be known. Ant Manor July 18th answers are known.
Jul 17, 2025 am 06:08 AM
Did you know? The evacuation doors for safe exits in public places should be known. Ant Manor July 18th answers are known.
Jul 17, 2025 am 06:08 AM
Maybe many friends want to know, do you know? The evacuation doors for safe exits in public places should be known. Ant Manor’s answer on July 18th is known. The editor below will bring you answers in this regard, hoping that it can help you!





