
ForbesGoogle Confirms New Hacker Protection For 3 Billion Android UsersBy Davey WinderFrom Vibe Coding To Vibe Hacking — The Reality Of AI In Cyberattacks
Vibe coding isn't exactly what many people believe it to be. I've come across several individuals, some of whom should know better, describing it as a way for AI to create code from scratch and build an entire application without any input from the person managing the process. Obviously, this is a distorted idea mixed with some truth. Vibe coding simplifies the work of developers by assigning parts of the programming to AI based on desired results, but it doesn’t eliminate the need for guidance or expertise. Still, LLMs and vibe coding are advancing rapidly and producing surprisingly effective code. But what if hackers started using similar methods—vibe hacking, so to speak—to carry out cyberattacks? Could they use LLMs to identify and exploit weaknesses effectively and maliciously?
Michele Campobasso, a senior security researcher at Forescout, says there's “no concrete evidence of real threat actors” doing this yet. He explains that most reports associate LLM usage with language-focused tasks like phishing, influence campaigns, explaining vulnerabilities, or creating standard malware components. Based on Campobasso’s recent analysis, vibe hacking still has a long way to go before catching up to vibe coding.
ForbesNew Bluetooth Headphones Spy Hack Warning — Are Yours On The List?By Davey Winder"During February through April 2025," Campobasso stated, "we evaluated more than 50 AI models across four test scenarios derived from industry-standard datasets and cybersecurity exercises." The findings were quite revealing:
- Open-source LLMs struggled across all tasks, proving “unsuitable even for basic vulnerability research.”
- Underground, criminal LLMs did slightly better but faced “usability problems such as limited access, unstable performance, poor formatting, and short context limits.”
- Commercial models naturally performed the best, though only three out of 18 managed to develop a working exploit for the hardest test case.
- Overall, LLMs found exploit creation far more difficult than identifying vulnerabilities, with none completing all assigned tasks.
Campobasso noted, “Attackers can't depend on one tool to handle the entire exploitation process.” Results were inconsistent and failure rates high. “Even when models succeeded in developing exploits,” he added, “they required significant user assistance.”
In summary, Campobasso emphasized that we're “still far from having LLMs capable of independently generating fully functional exploits.” Additionally, the misleading confidence expressed by these models when wrong could easily mislead novice attackers who rely heavily on them.
The era of vibe hacking is on the horizon, though not progressing as quickly as vibe coding might suggest, and defenders should begin preparing now. Fortunately, this doesn’t have to be complicated, according to Campobasso. “Cybersecurity fundamentals remain the same: An AI-generated exploit is still an exploit, which means it can be detected, blocked, or neutralized through patching.”
ForbesUse These Secret Gmail Addresses To Prevent Hack Attacks — Here’s HowBy Davey Winder
The above is the detailed content of From Vibe Coding To Vibe Hacking — AI In A Hoodie. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 AI Investor Stuck At A Standstill? 3 Strategic Paths To Buy, Build, Or Partner With AI Vendors
Jul 02, 2025 am 11:13 AM
AI Investor Stuck At A Standstill? 3 Strategic Paths To Buy, Build, Or Partner With AI Vendors
Jul 02, 2025 am 11:13 AM
Investing is booming, but capital alone isn’t enough. With valuations rising and distinctiveness fading, investors in AI-focused venture funds must make a key decision: Buy, build, or partner to gain an edge? Here’s how to evaluate each option—and pr
 AGI And AI Superintelligence Are Going To Sharply Hit The Human Ceiling Assumption Barrier
Jul 04, 2025 am 11:10 AM
AGI And AI Superintelligence Are Going To Sharply Hit The Human Ceiling Assumption Barrier
Jul 04, 2025 am 11:10 AM
Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining various impactful AI complexities (see the link here). Heading Toward AGI And
 Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Remember the flood of open-source Chinese models that disrupted the GenAI industry earlier this year? While DeepSeek took most of the headlines, Kimi K1.5 was one of the prominent names in the list. And the model was quite cool.
 Future Forecasting A Massive Intelligence Explosion On The Path From AI To AGI
Jul 02, 2025 am 11:19 AM
Future Forecasting A Massive Intelligence Explosion On The Path From AI To AGI
Jul 02, 2025 am 11:19 AM
Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining various impactful AI complexities (see the link here). For those readers who h
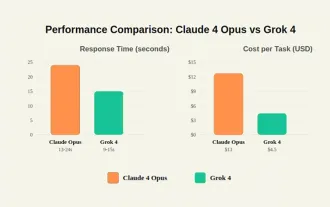 Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
By mid-2025, the AI “arms race” is heating up, and xAI and Anthropic have both released their flagship models, Grok 4 and Claude 4. These two models are at opposite ends of the design philosophy and deployment platform, yet they
 Chain Of Thought For Reasoning Models Might Not Work Out Long-Term
Jul 02, 2025 am 11:18 AM
Chain Of Thought For Reasoning Models Might Not Work Out Long-Term
Jul 02, 2025 am 11:18 AM
For example, if you ask a model a question like: “what does (X) person do at (X) company?” you may see a reasoning chain that looks something like this, assuming the system knows how to retrieve the necessary information:Locating details about the co
 Senate Kills 10-Year State-Level AI Ban Tucked In Trump's Budget Bill
Jul 02, 2025 am 11:16 AM
Senate Kills 10-Year State-Level AI Ban Tucked In Trump's Budget Bill
Jul 02, 2025 am 11:16 AM
The Senate voted 99-1 Tuesday morning to kill the moratorium after a last-minute uproar from advocacy groups, lawmakers and tens of thousands of Americans who saw it as a dangerous overreach. They didn’t stay quiet. The Senate listened.States Keep Th
 This Startup Built A Hospital In India To Test Its AI Software
Jul 02, 2025 am 11:14 AM
This Startup Built A Hospital In India To Test Its AI Software
Jul 02, 2025 am 11:14 AM
Clinical trials are an enormous bottleneck in drug development, and Kim and Reddy thought the AI-enabled software they’d been building at Pi Health could help do them faster and cheaper by expanding the pool of potentially eligible patients. But the






