
But that’s changing—thanks in large part to a fundamental shift in how we interpret and respond to risk.
The Cloud Visibility Gap Is a Threat Vector in Itself
Hybrid and multi-cloud environments have become the new normal.
Organizations run workloads across AWS, Azure, Google Cloud, and on-prem data centers—all while managing sprawling APIs, ephemeral containers, and third-party integrations. The result is a security visibility crisis.
Traditional Network Detection and Response tools can’t scale across cloud providers. Cloud-native application protection platforms, meanwhile, offer great telemetry—if you're entirely in the cloud. But most enterprises aren’t. And even when these platforms work as advertised, they often lack the context needed to act.
“There are really two fundamental issues here,” explains Jon Oltsik, analyst in residence at SiliconANGLE and theCUBE. “One is real-time visibility across all associated assets and components. The other is the ability to add context—such as an asset’s location, vulnerability, business value, etc. This visibility and context really requires massive scale and superior analytics.”
As Mario Espinoza, Chief Product Officer at Illumio, put it: “A breach doesn’t have to become a cyber disaster. But you can’t stop what you can’t see—and you can’t contain what you don’t understand.”
In short, detection isn’t enough. To mount an effective defense, you need to understand what’s happening—and why it matters.
Why Conventional Tools Fall Short
Let’s break it down:
- NDR tools rely on perimeter traffic and predefined rules. That’s great for well-understood threats, but attackers today exploit complexity and blind spots—especially through lateral movement.
- CNAPPs focus primarily on posture and configuration. They often miss the real-time activity that indicates an attack in progress.
- Both tend to overwhelm SOCs with high volumes of alerts while offering little guidance on what matters or what to do next.
And here's the hard truth: even the best-prevention strategy eventually fails. Breaches are inevitable. The real question is—what happens next?
Enter the AI Security Graph
The answer is the AI security graph, a data model that maps every workload, resource, and connection across the environment—on-prem and in the cloud. Think of it as a living, evolving blueprint of your organization’s digital nervous system.
By layering AI on top of this graph, organizations can detect previously invisible patterns, such as stealthy lateral movement or anomalous traffic between systems that should never be communicating.
Putting It Into Practice
This isn’t just theoretical. Illumio Insights brings the AI security graph to life. Espinoza explains it this way: “The attacker sees your network as a graph. Until now, defenders have been stuck thinking in lists. We’re changing that.”
Espinoza explained to me that Illumio Insights ingests billions of flows across hybrid and multi-cloud environments, in real time, without the need for agents or invasive infrastructure changes. The platform analyzes that data to identify blast radius, high-value targets under attack, and even obscure threats like shadow LLM activity or policy violations that expose critical workloads.
“We compress what could be hundreds of thousands of flows into a single, meaningful insight,” Espinoza notes. “Instead of overwhelming the SOC with alerts, we deliver a distilled view of what’s actually going on—and what needs to happen next.”
This approach doesn’t just reduce alert fatigue. It has the potential to fundamentally changes the nature of incident response. Analysts no longer need to sift through raw logs or stitch together disjointed alerts. They simply get an immediate, contextualized picture—with the ability to act on it instantly.
From Insight to Action
According to Espinoza, one of the most powerful features of Illumio Insights is its integration with Illumio Segmentation. With a single click, security teams can dynamically quarantine compromised systems—restricting communication without disrupting operations. Espinoza calls it "surgical enforcement."
“You might see a suspicious machine,” he explains, “but instead of shutting it down entirely and risking business disruption, you isolate the threat by disabling just the risky communication paths. It's like neurosurgery instead of amputation.”
That level of precision is critical in sensitive environments like manufacturing, energy, and healthcare—where taking a system offline isn’t just inconvenient, it’s potentially catastrophic.
Rethinking the Security Workflow
Perhaps most compelling is the flexibility that Illumio Insights offers. Organizations can deploy it in read-only mode for observability, integrate it into existing SIEM and SOAR workflows, or let it autonomously take action based on pre-approved rules. And as Espinoza shared, many customers who start with observability quickly ask to move into enforcement once they “see the full picture.”
Interestingly, while segmentation was originally positioned as a proactive Zero Trust control, it's the incident responders and threat hunters who have driven adoption of Insights. "They saw the gold mine in the graph,” Espinoza says. “They didn’t want to wait for a segmentation strategy—they wanted visibility and insights now.”
According to Oltsik, the real differentiator is how Illumio connects detection to enforcement in a seamless loop. “The beauty with Illumio is that it connects this detection and analysis with remediation capabilities. So, when Insights detects malicious traffic, security teams can further segment networks to prevent any further damage. This is an element of cyber-resilience—the ability to recover quickly from a cyberattack while minimizing damages.”
Smarter, Connected Graphs
Illumio isn’t stopping with network flows. Espinoza also hinted at a future where Illumio Insights connects with other graphs—like Microsoft’s and CrowdStrike’s—to offer even deeper context and automation.
The vision is clear: to arm defenders with tools that not only match, but surpass, the sophistication of modern attackers. “This is how we turn the tide,” he says. “Security at a system level. Defense that understands the environment better than the adversary does.”
From Reaction to Resilience
Organizations need something that is both profound and practical: a unified, intelligent view of the environment that empowers security teams to detect, understand, and contain threats—before they spiral into full-blown crises.
Because in a world where attackers think in graphs, it’s time defenders started doing the same.
The above is the detailed content of Rethinking Threat Detection In A Decentralized World. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 AI Investor Stuck At A Standstill? 3 Strategic Paths To Buy, Build, Or Partner With AI Vendors
Jul 02, 2025 am 11:13 AM
AI Investor Stuck At A Standstill? 3 Strategic Paths To Buy, Build, Or Partner With AI Vendors
Jul 02, 2025 am 11:13 AM
Investing is booming, but capital alone isn’t enough. With valuations rising and distinctiveness fading, investors in AI-focused venture funds must make a key decision: Buy, build, or partner to gain an edge? Here’s how to evaluate each option—and pr
 AGI And AI Superintelligence Are Going To Sharply Hit The Human Ceiling Assumption Barrier
Jul 04, 2025 am 11:10 AM
AGI And AI Superintelligence Are Going To Sharply Hit The Human Ceiling Assumption Barrier
Jul 04, 2025 am 11:10 AM
Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining various impactful AI complexities (see the link here). Heading Toward AGI And
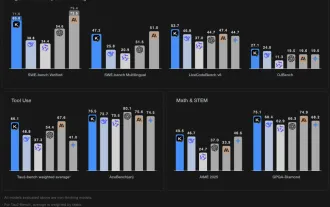 Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Remember the flood of open-source Chinese models that disrupted the GenAI industry earlier this year? While DeepSeek took most of the headlines, Kimi K1.5 was one of the prominent names in the list. And the model was quite cool.
 Future Forecasting A Massive Intelligence Explosion On The Path From AI To AGI
Jul 02, 2025 am 11:19 AM
Future Forecasting A Massive Intelligence Explosion On The Path From AI To AGI
Jul 02, 2025 am 11:19 AM
Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining various impactful AI complexities (see the link here). For those readers who h
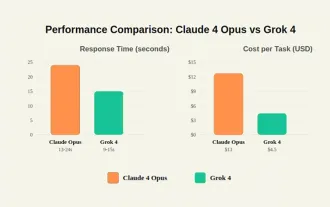 Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
By mid-2025, the AI “arms race” is heating up, and xAI and Anthropic have both released their flagship models, Grok 4 and Claude 4. These two models are at opposite ends of the design philosophy and deployment platform, yet they
 Chain Of Thought For Reasoning Models Might Not Work Out Long-Term
Jul 02, 2025 am 11:18 AM
Chain Of Thought For Reasoning Models Might Not Work Out Long-Term
Jul 02, 2025 am 11:18 AM
For example, if you ask a model a question like: “what does (X) person do at (X) company?” you may see a reasoning chain that looks something like this, assuming the system knows how to retrieve the necessary information:Locating details about the co
 Senate Kills 10-Year State-Level AI Ban Tucked In Trump's Budget Bill
Jul 02, 2025 am 11:16 AM
Senate Kills 10-Year State-Level AI Ban Tucked In Trump's Budget Bill
Jul 02, 2025 am 11:16 AM
The Senate voted 99-1 Tuesday morning to kill the moratorium after a last-minute uproar from advocacy groups, lawmakers and tens of thousands of Americans who saw it as a dangerous overreach. They didn’t stay quiet. The Senate listened.States Keep Th
 This Startup Built A Hospital In India To Test Its AI Software
Jul 02, 2025 am 11:14 AM
This Startup Built A Hospital In India To Test Its AI Software
Jul 02, 2025 am 11:14 AM
Clinical trials are an enormous bottleneck in drug development, and Kim and Reddy thought the AI-enabled software they’d been building at Pi Health could help do them faster and cheaper by expanding the pool of potentially eligible patients. But the






